OBJECTIVES
By the end of this post you will be able to:
• Describe the main functionality of the CPM and PVWA
• How to Install the CPM and PVWA
• How to Secure and Harden the CPM and PVWA
Related Posts:
PVWA AND CPM FUNCTIONALITY
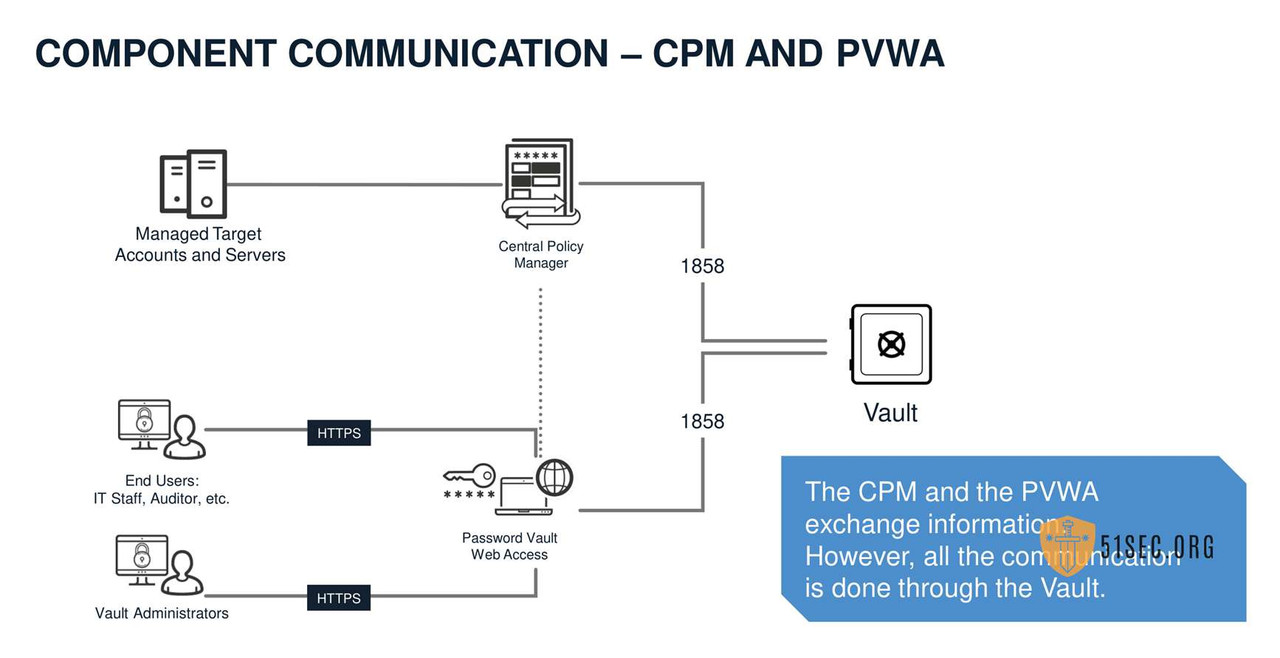
CENTRAL POLICY MANAGER
• The CPM is responsible for:
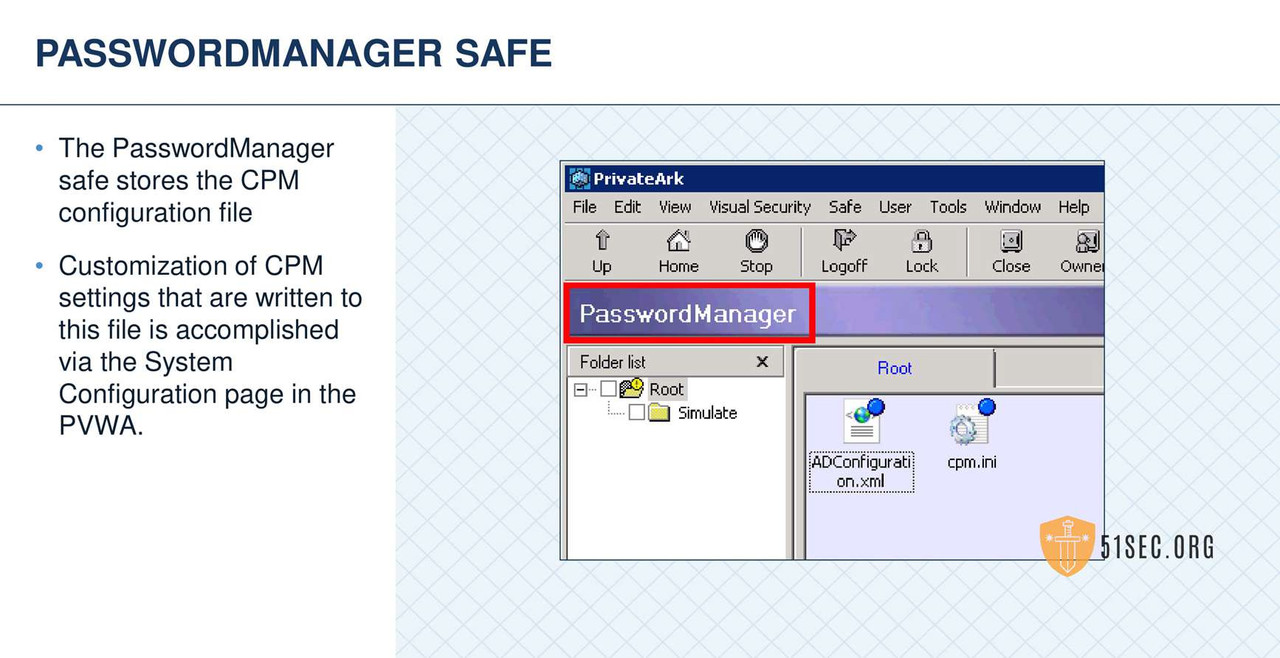
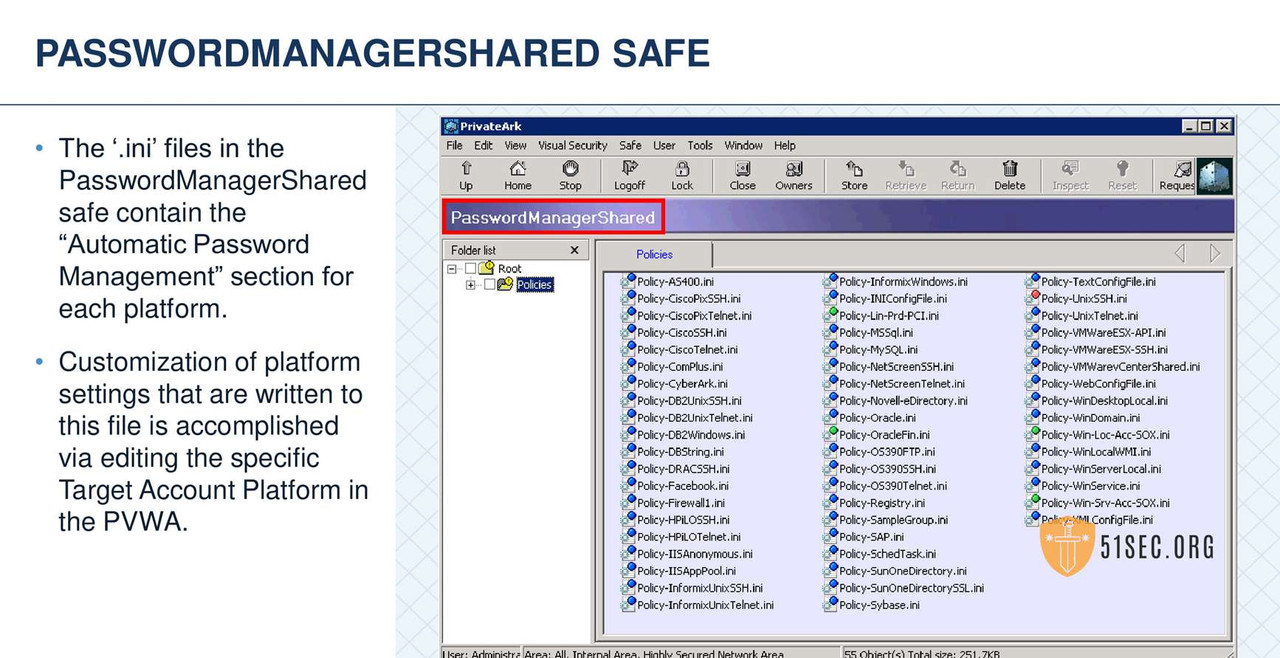
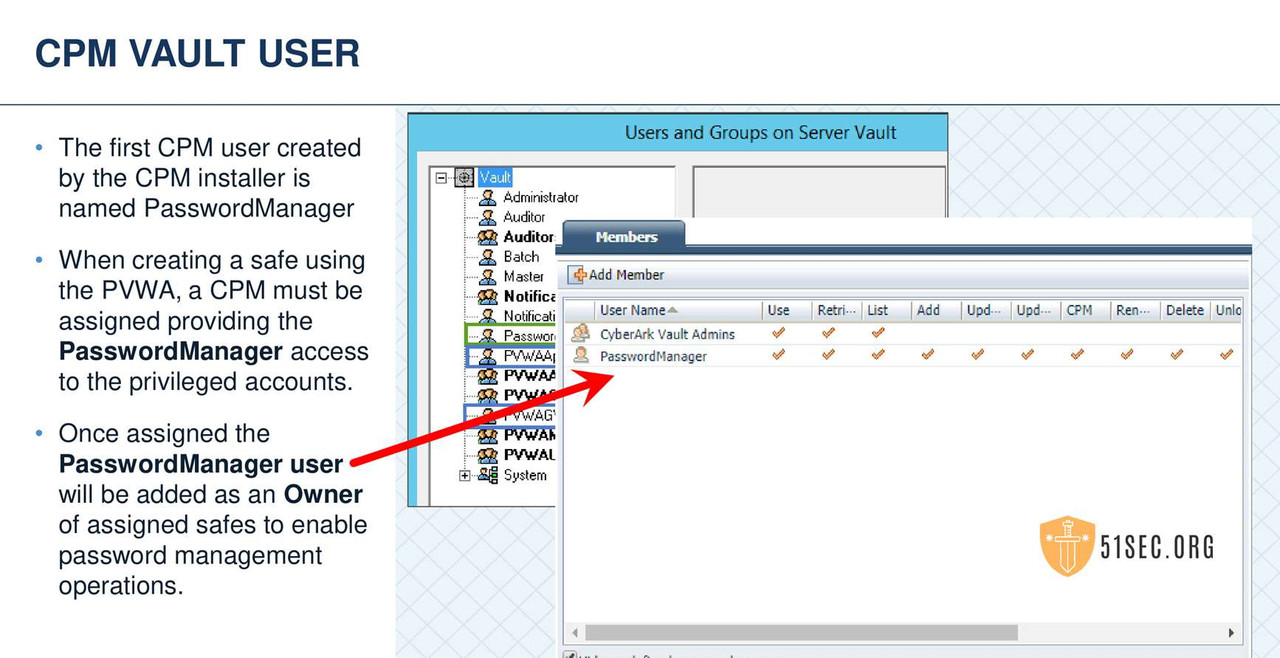
• Password Management Operations
- • Changing and verifying all target account password
- • Enforces Password Policy
• The CPM Accounts Feed and Auto Detection Operations
- • Discover Automate privileged account discovery, designed to quickly locate critical accounts and credentials.
- • Analyze Provides a view of all discovered accounts analysis to assess the risk of each account.
- • Provision Accounts targeted for management can be provisioned in the Vault in a simple and intuitive way.
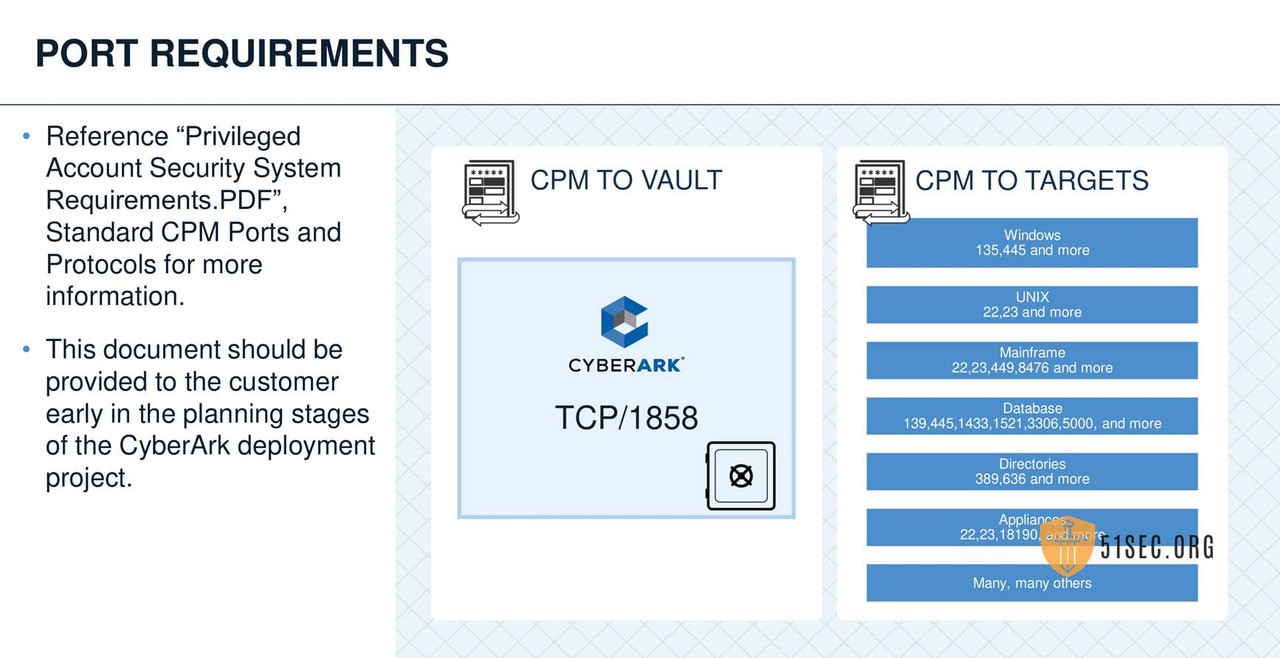
PVWA PREREQUISITES INSTALLATION
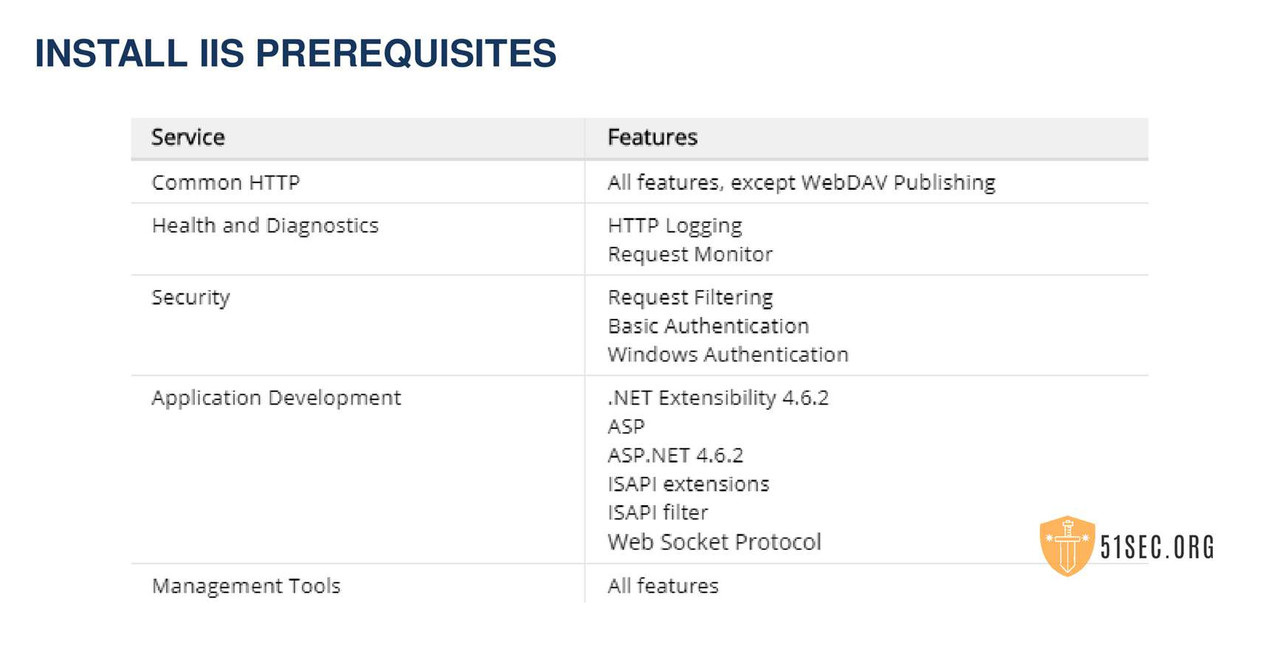
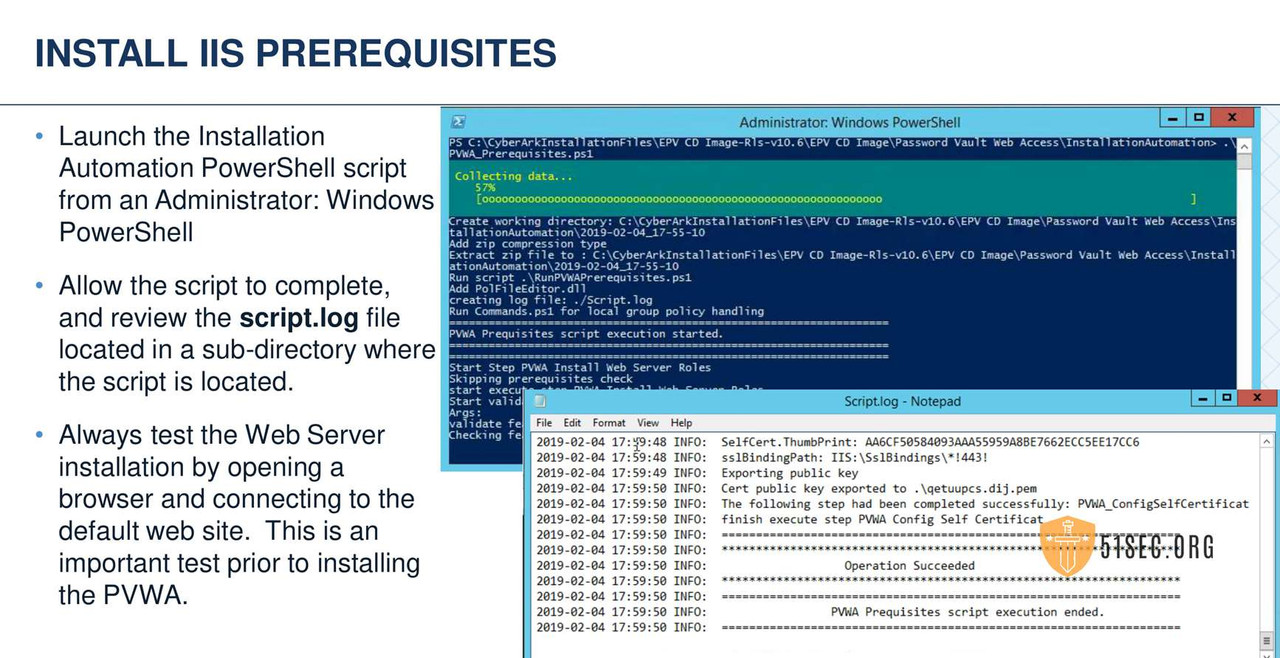
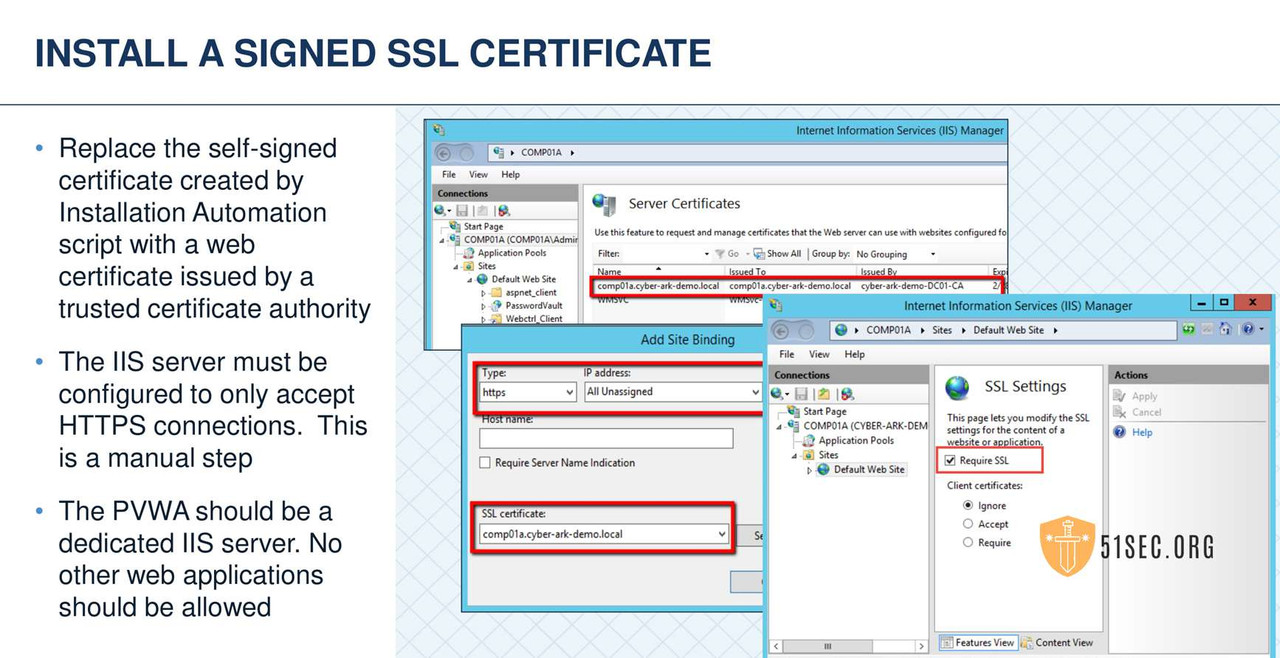
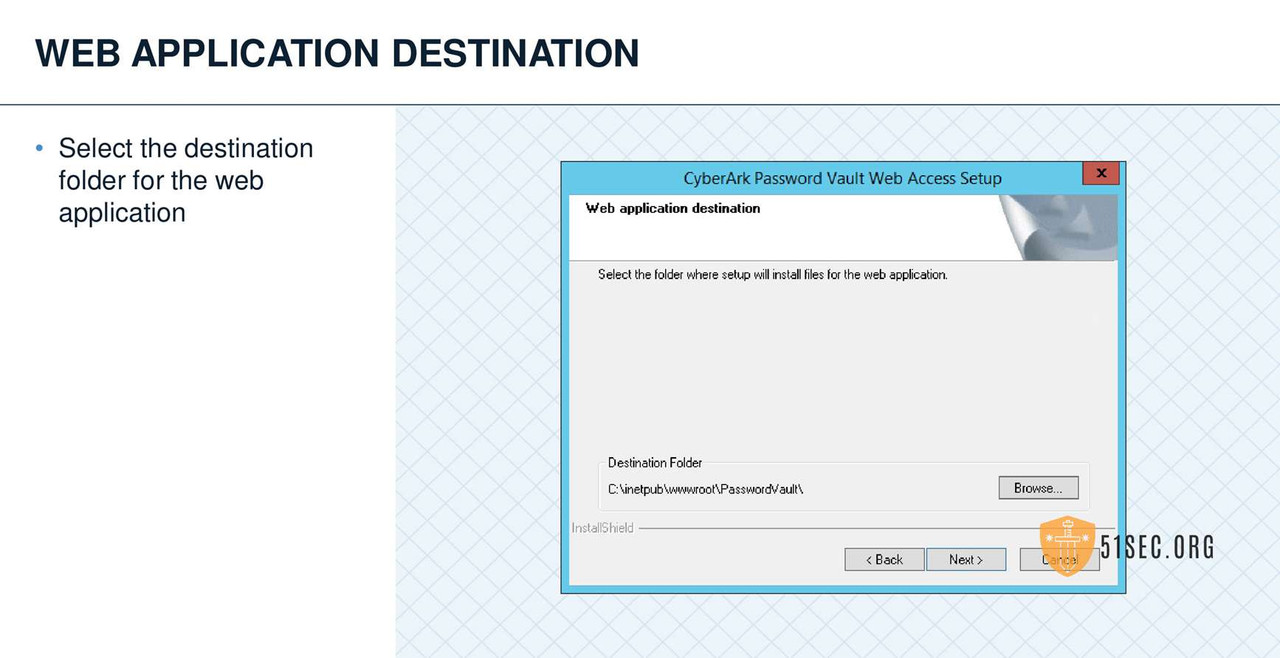
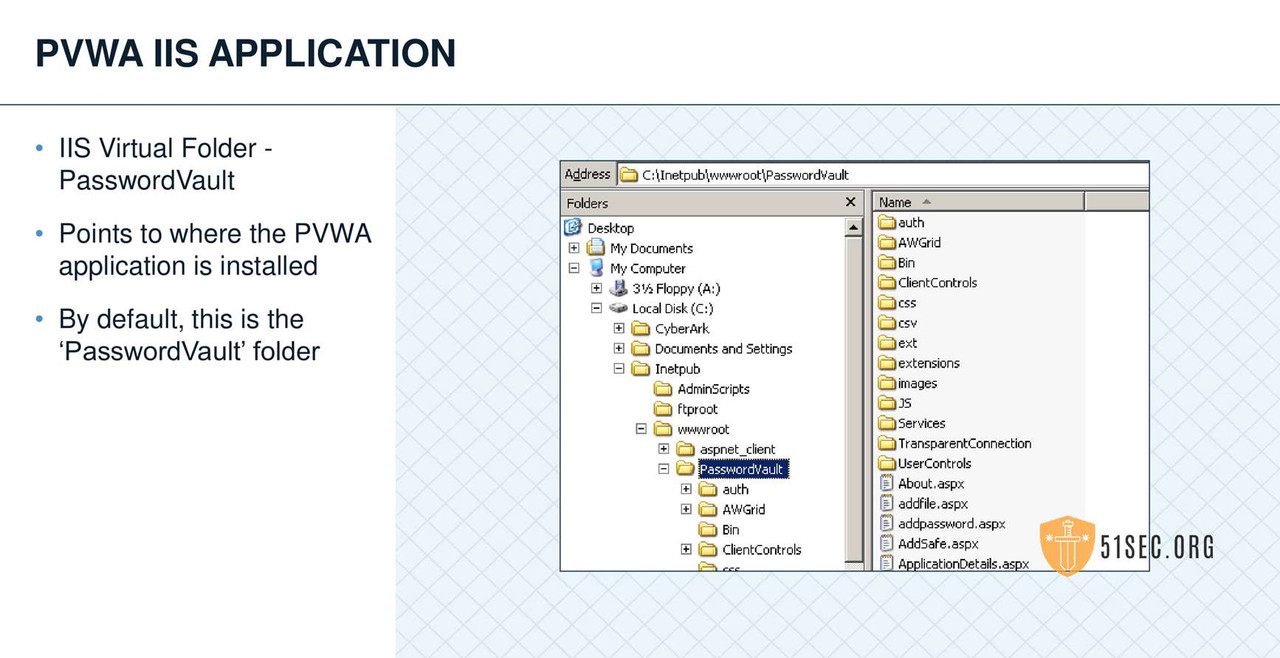
PVWA INSTALLATION
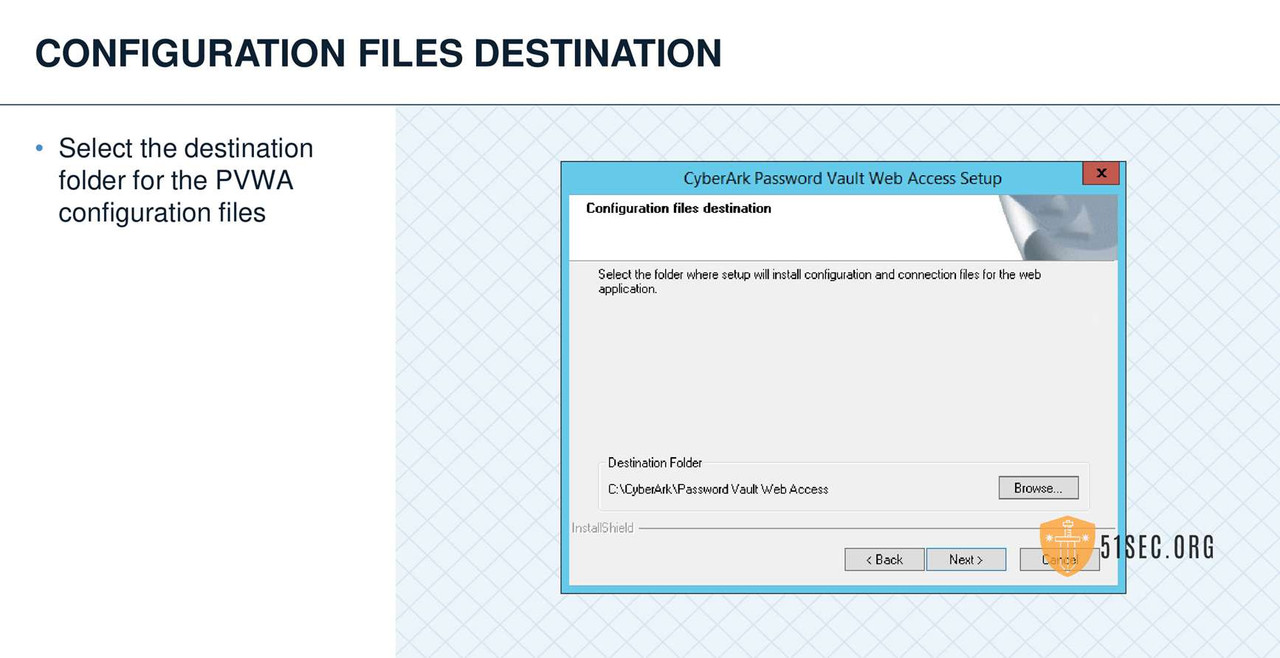
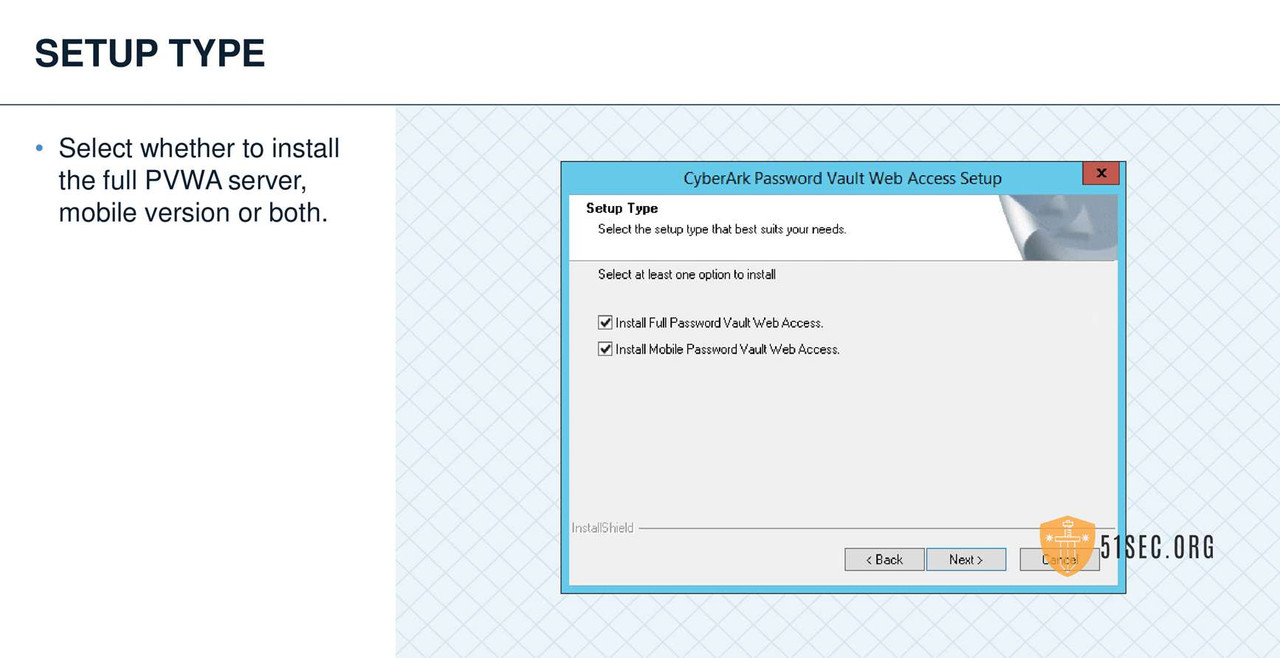
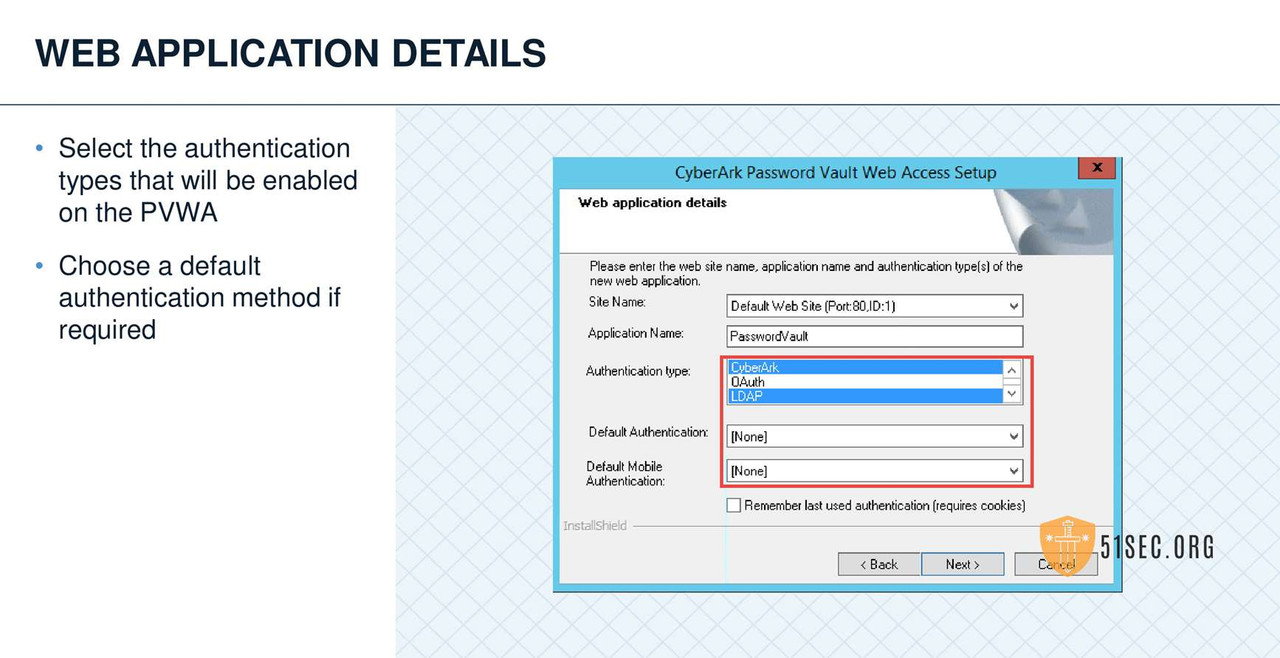
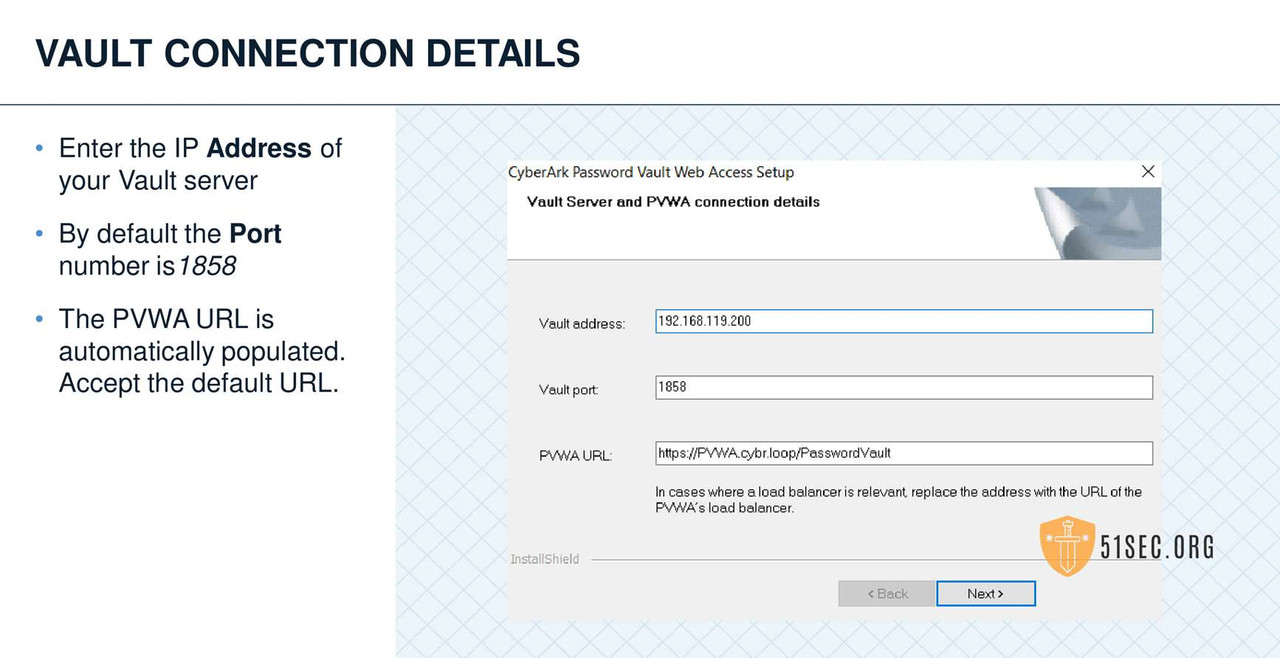
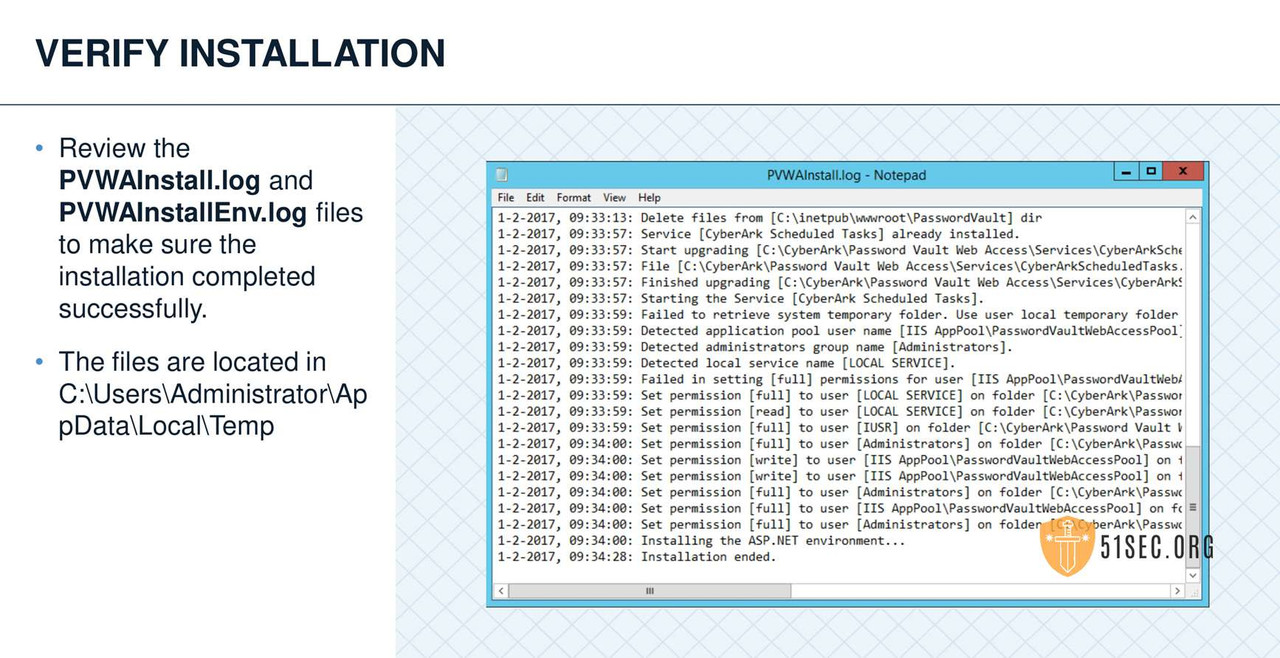
PVWA VERIFY SERVER ENVIRONMENT
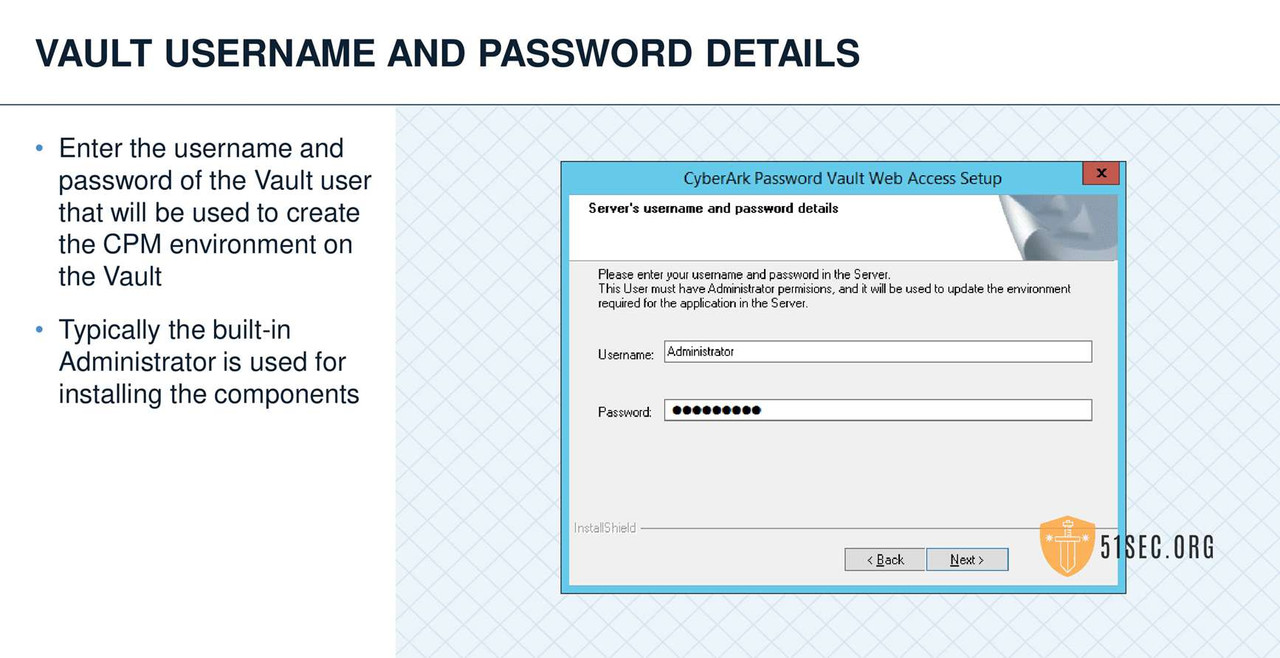
PVWA VERIFY VAULT ENVIRONMENT
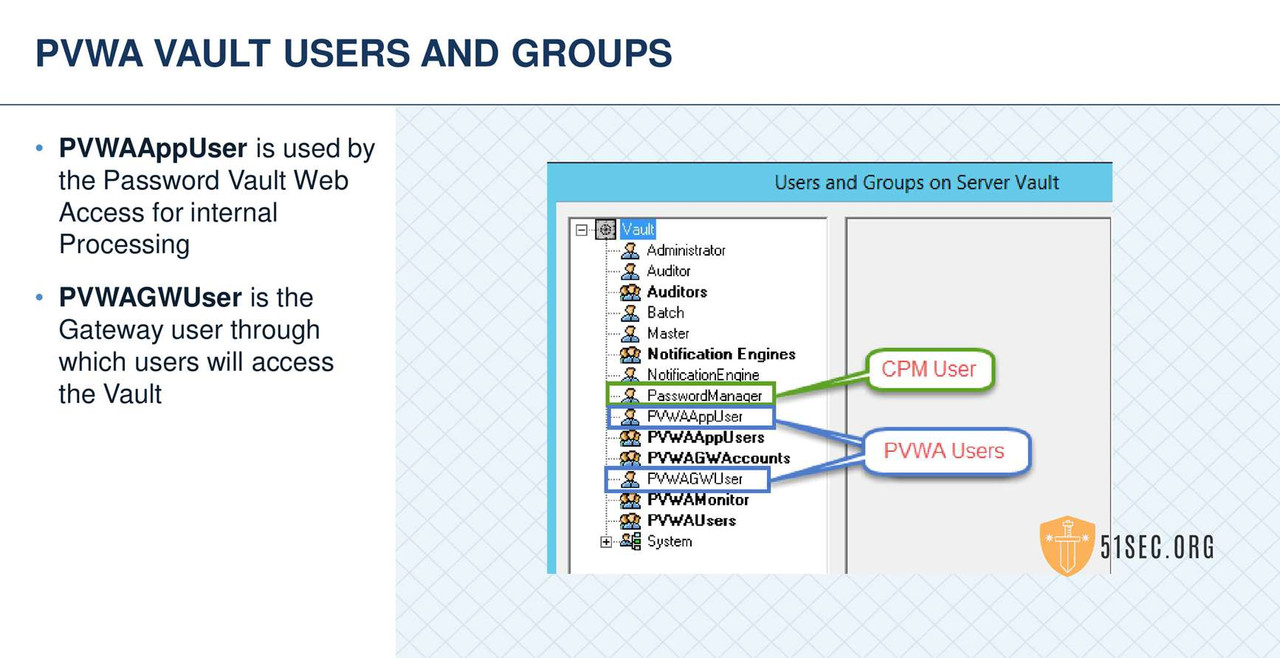
HARDENING THE PVWA
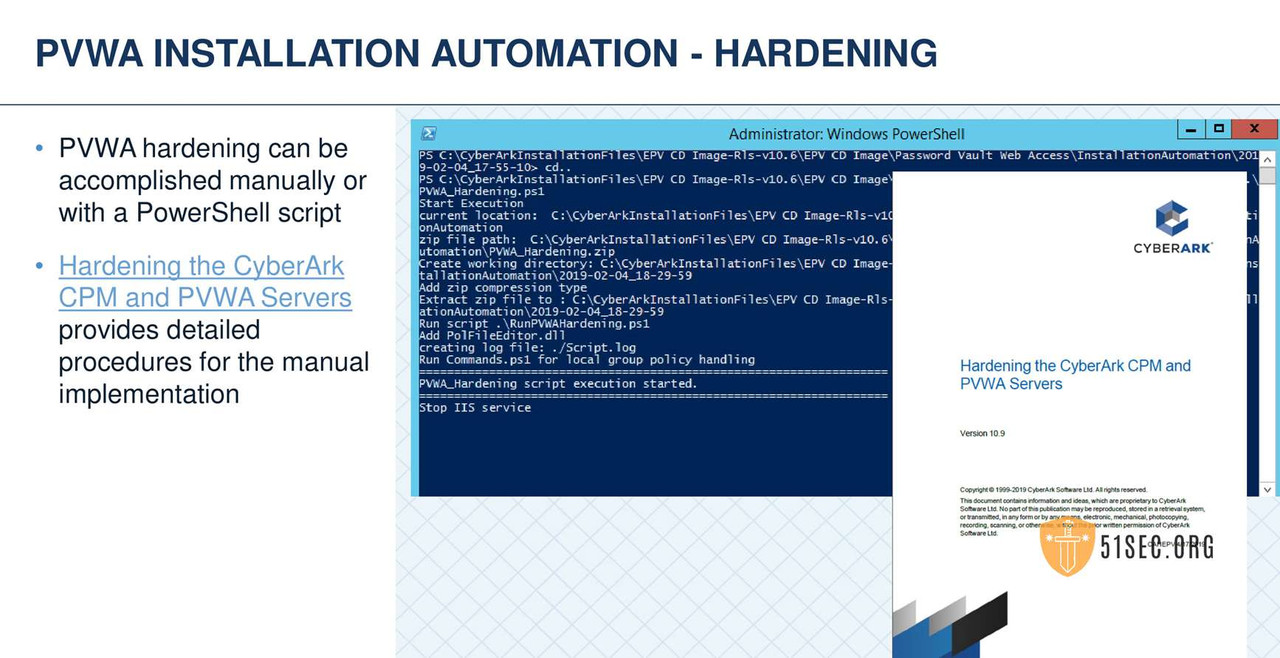
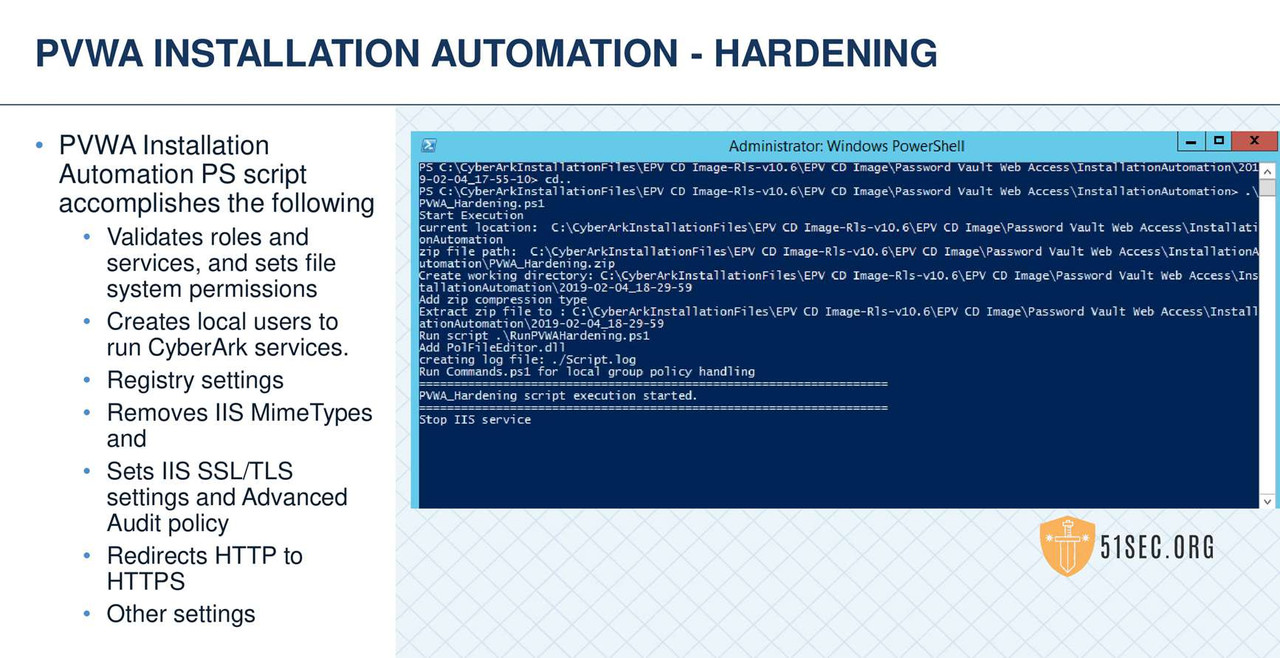
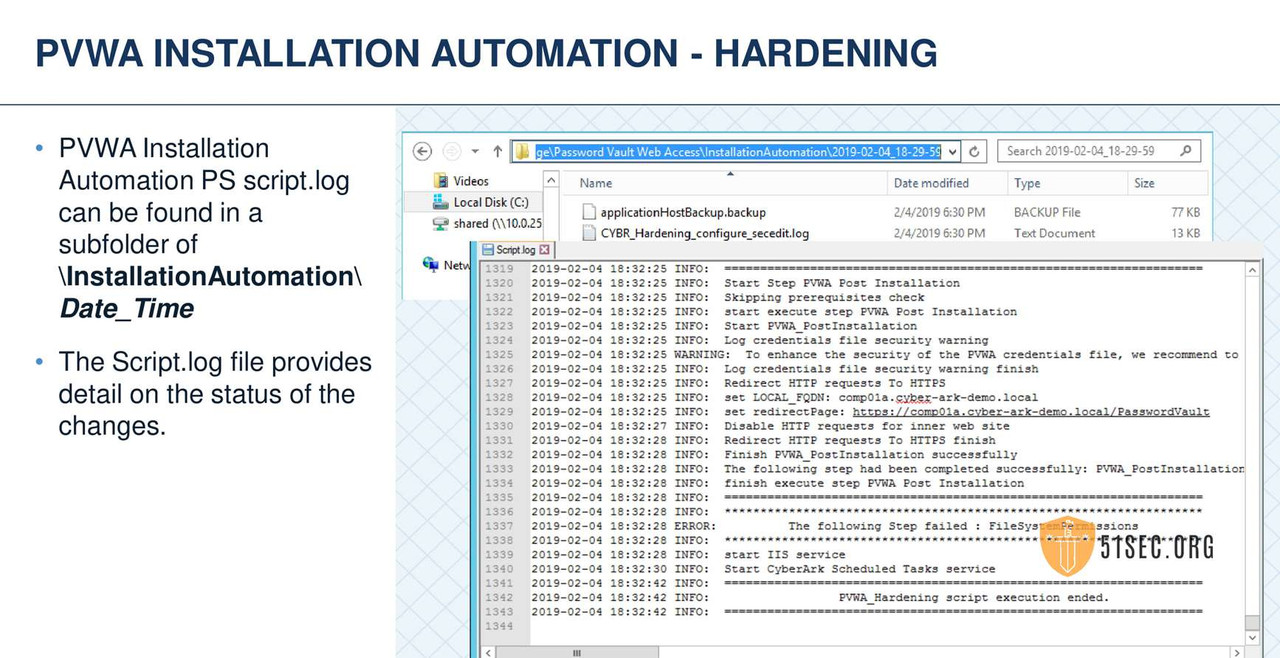
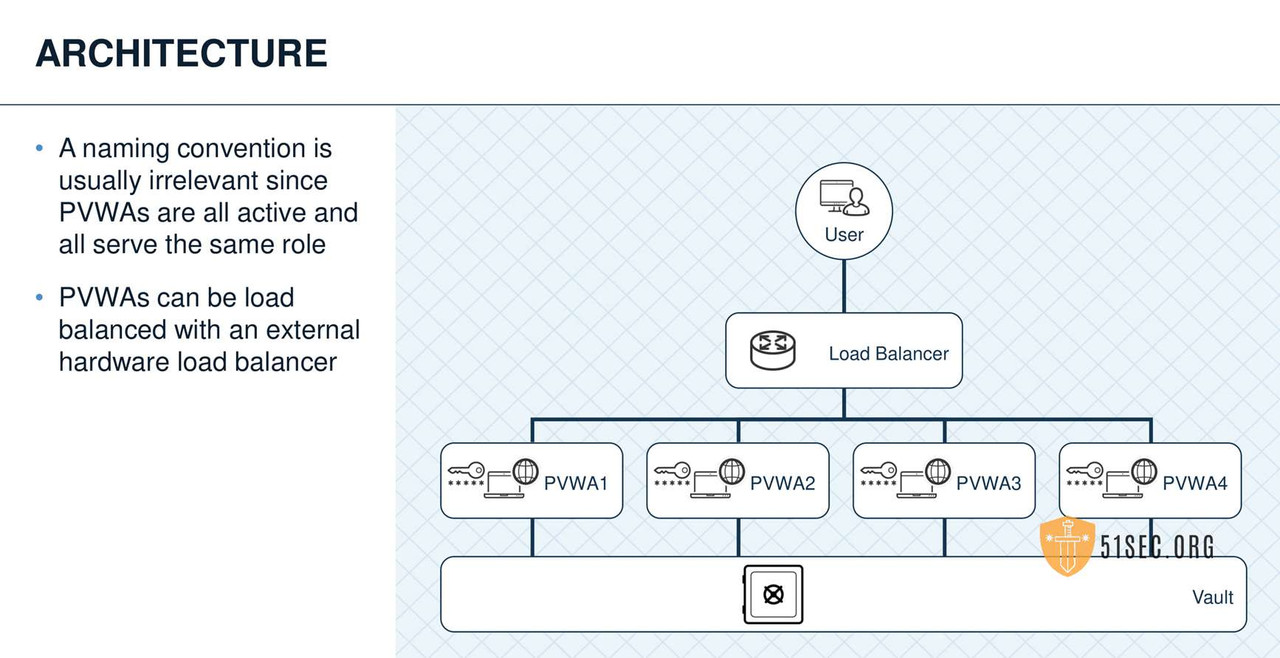
MULTIPLE PVWAS
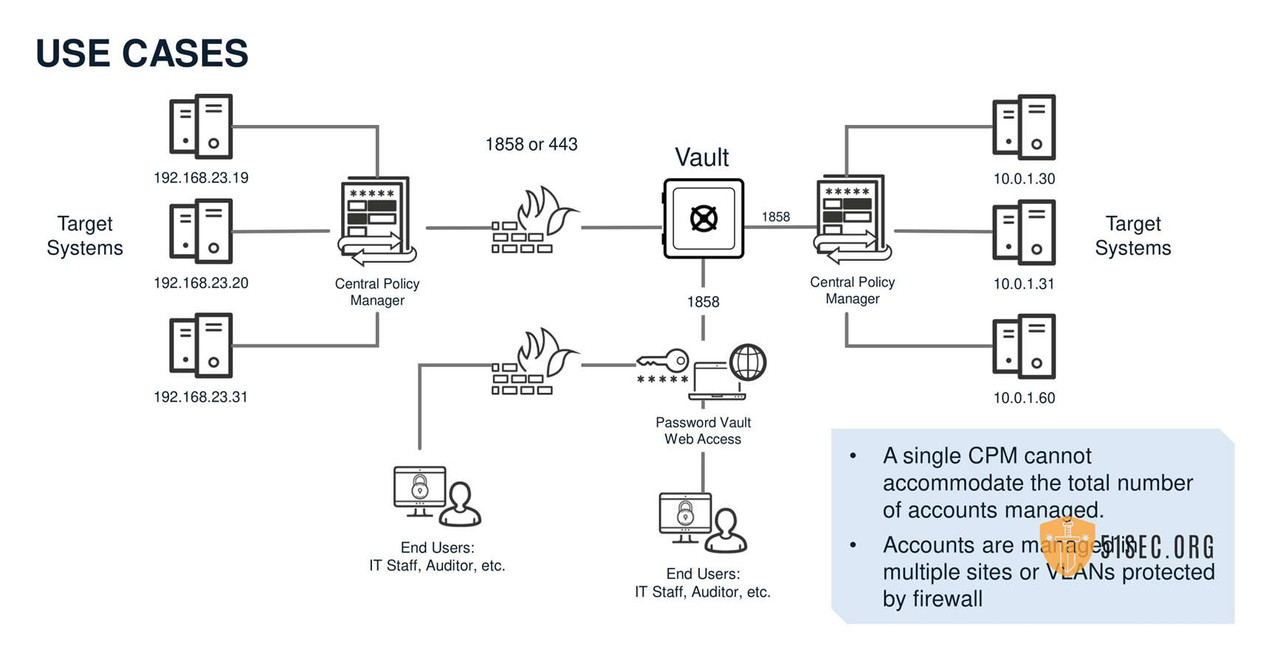
USE CASES
• Fault Tolerance and Disaster Recovery in the Web Interface
• Reduce web traffic over WAN lines
• Provide a second less privileged web interface for external users (vendors or contractors).
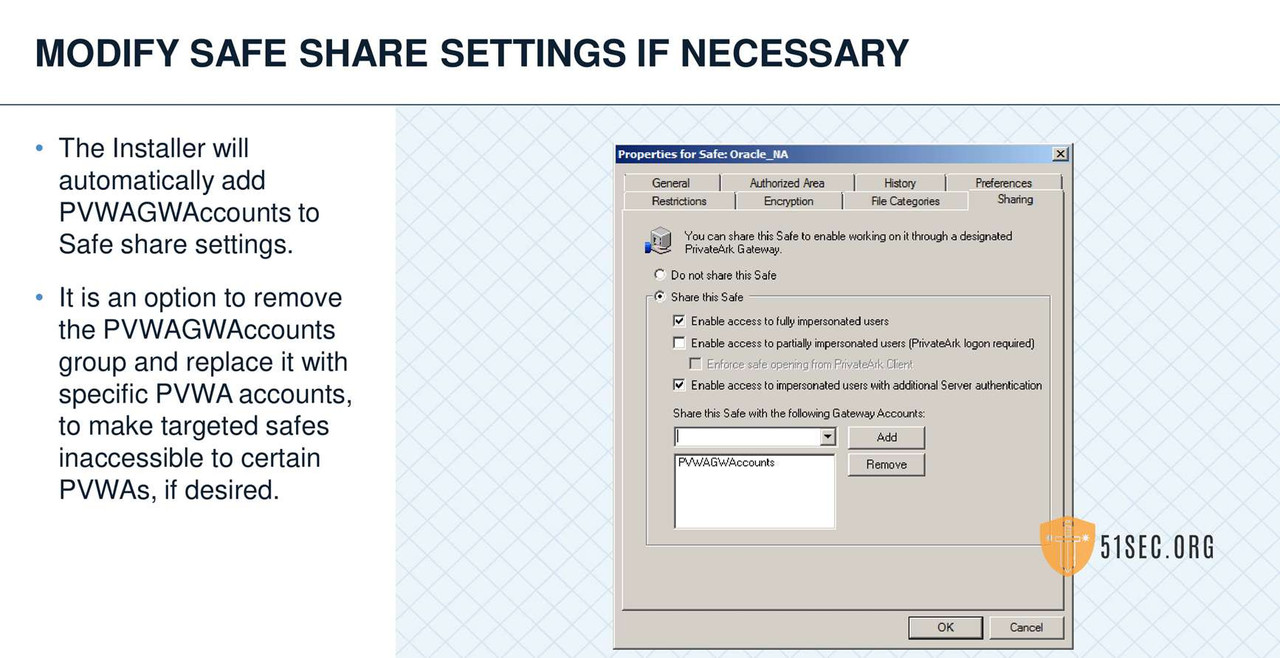
CPM INSTALLATION
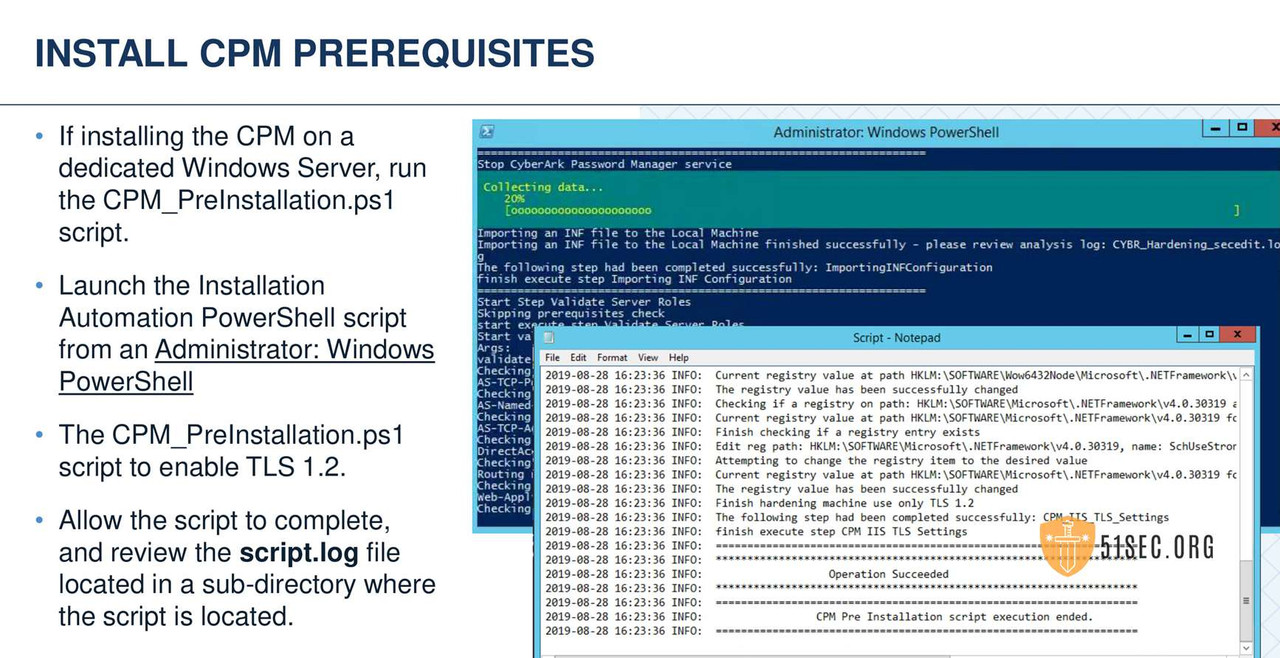
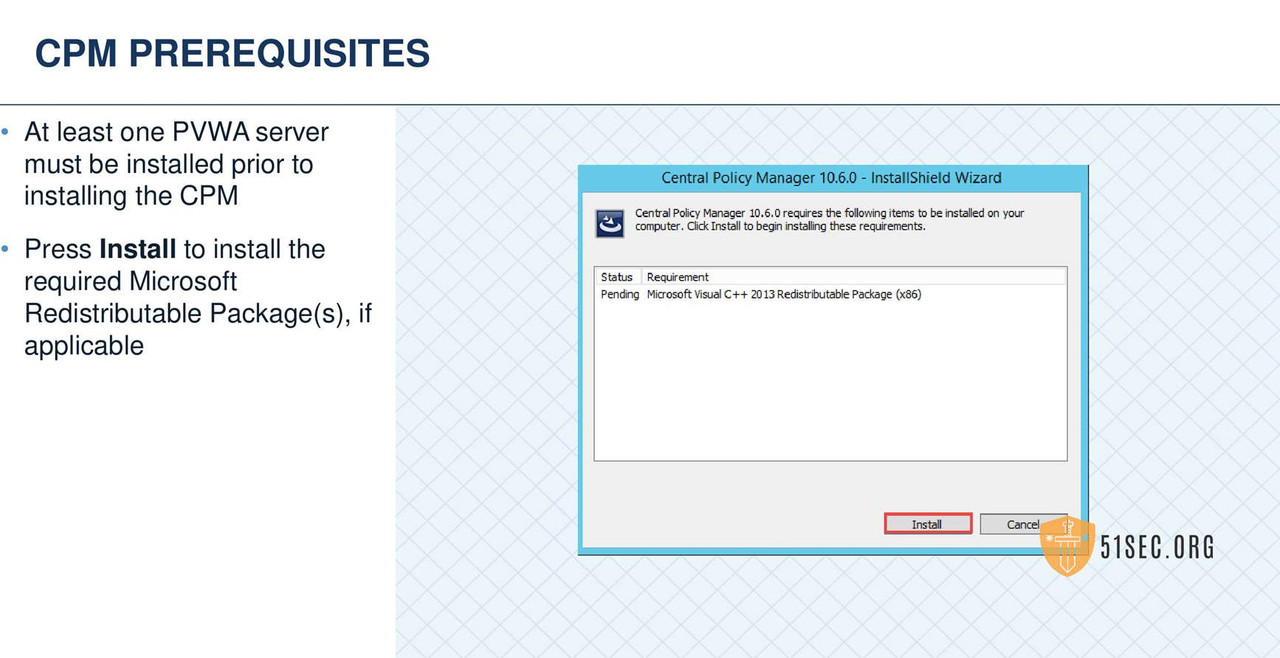
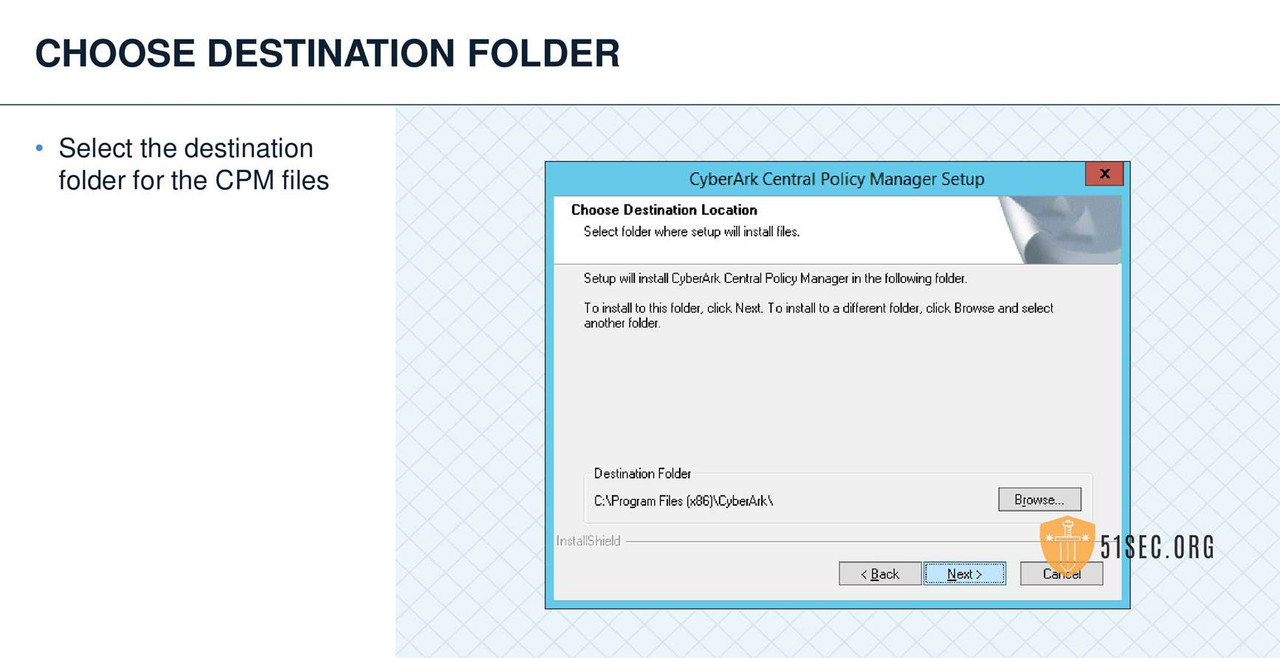
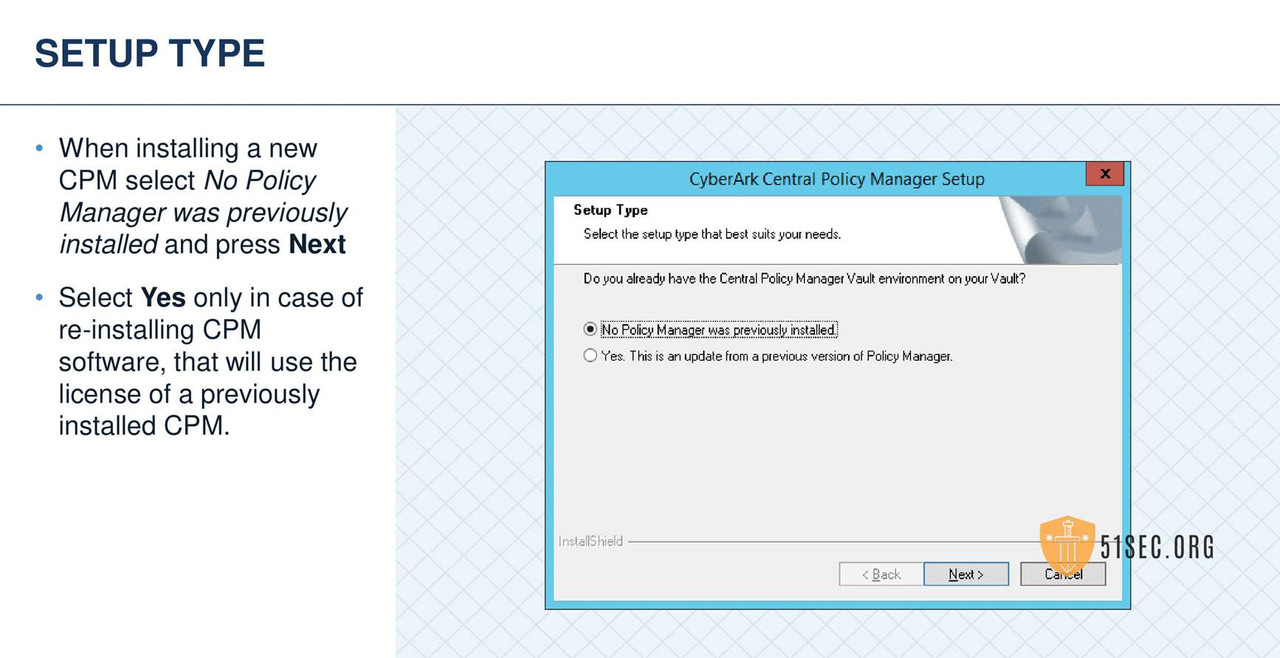
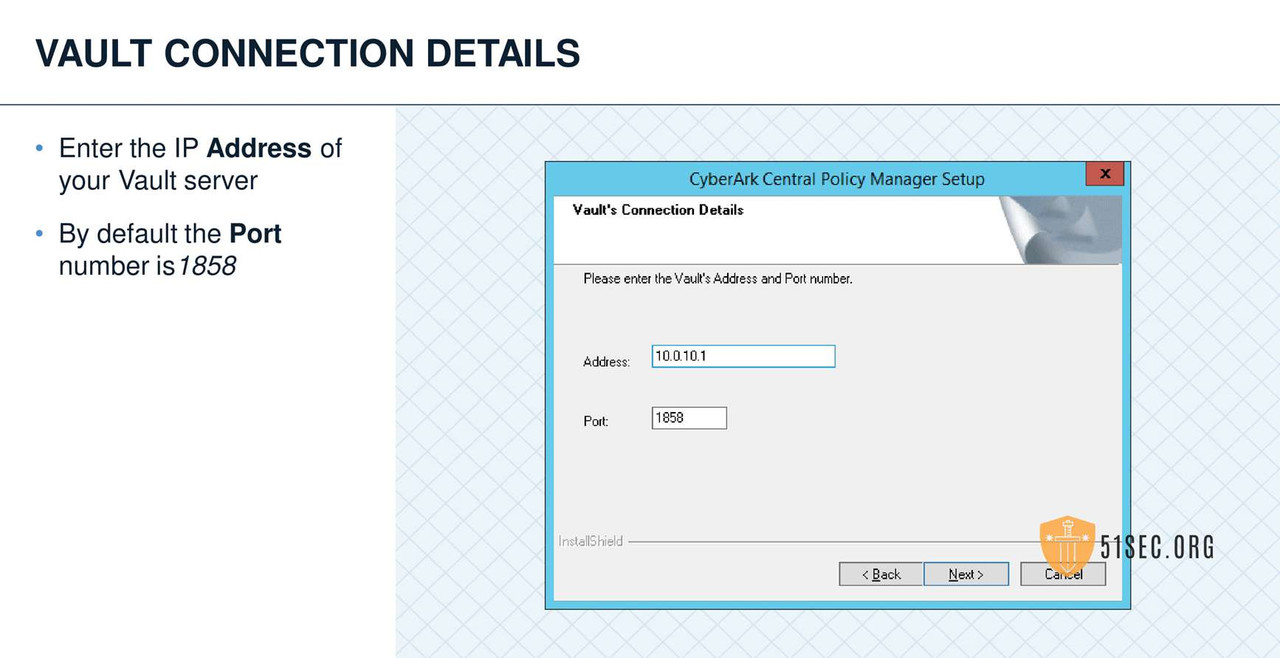
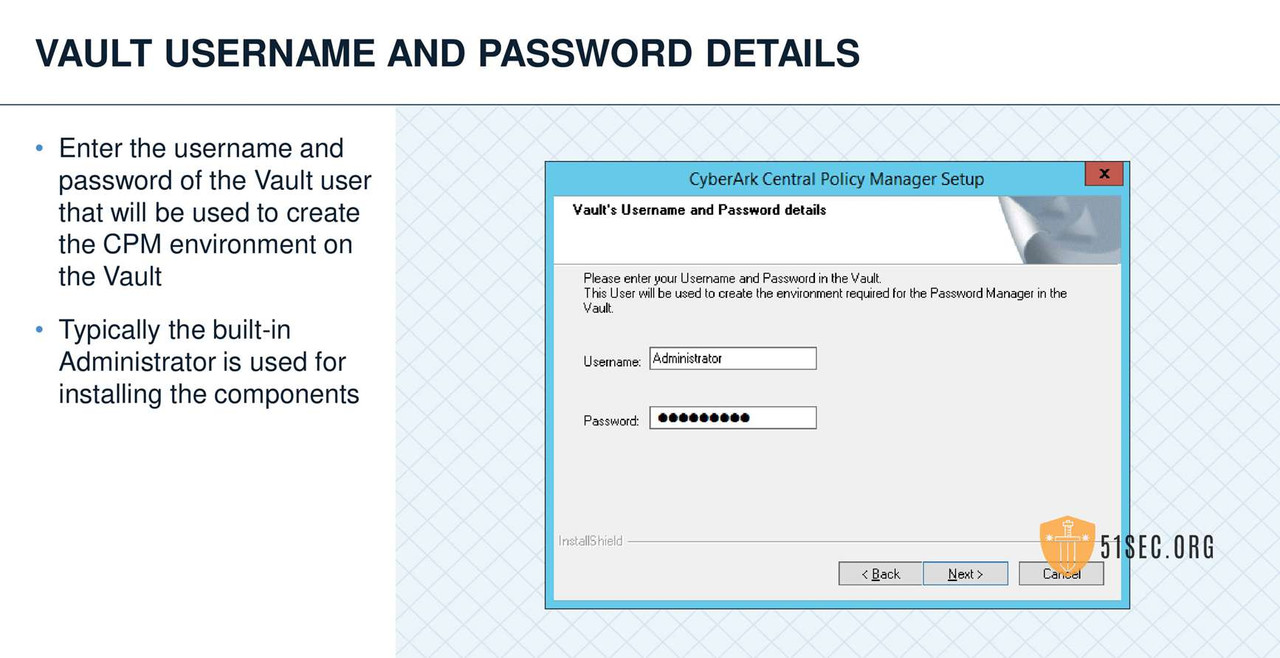
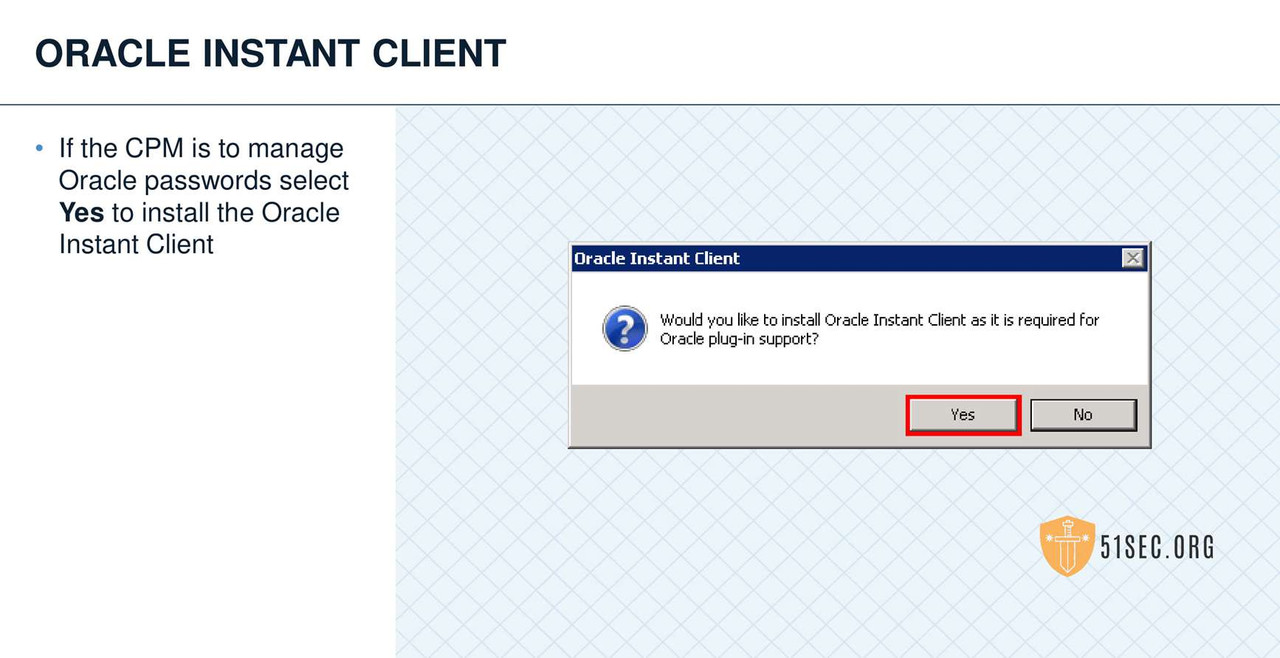
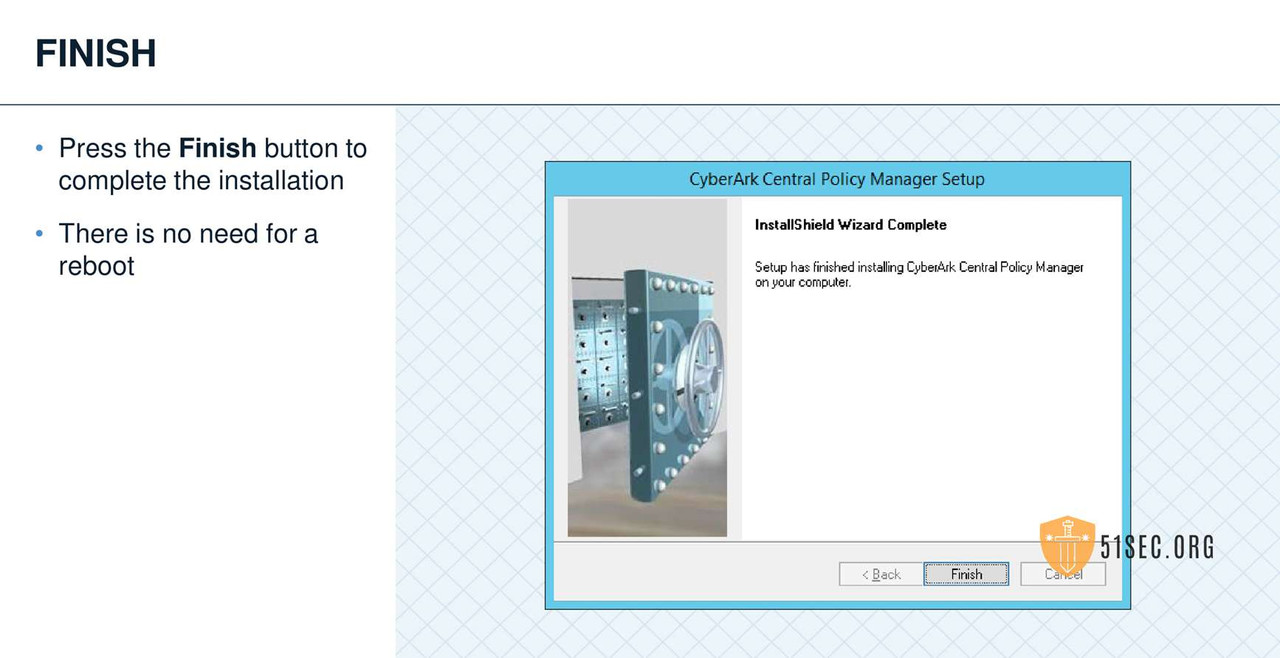
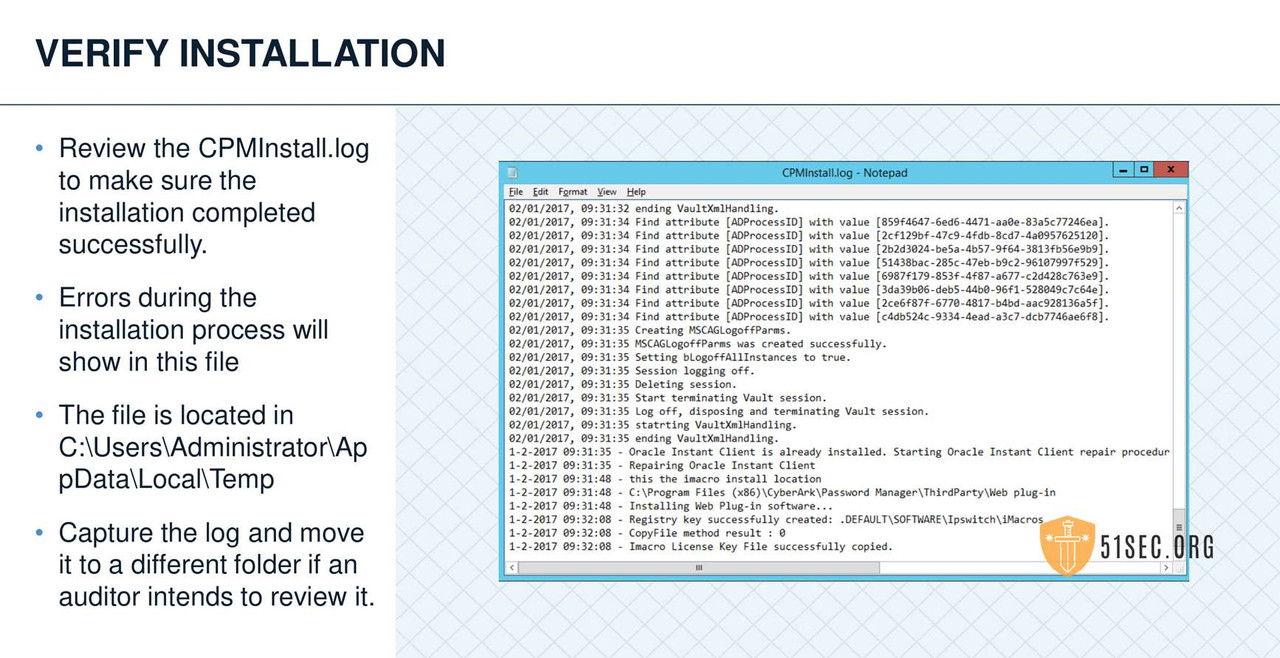
CPM VERIFY SERVER ENVIRONMENT
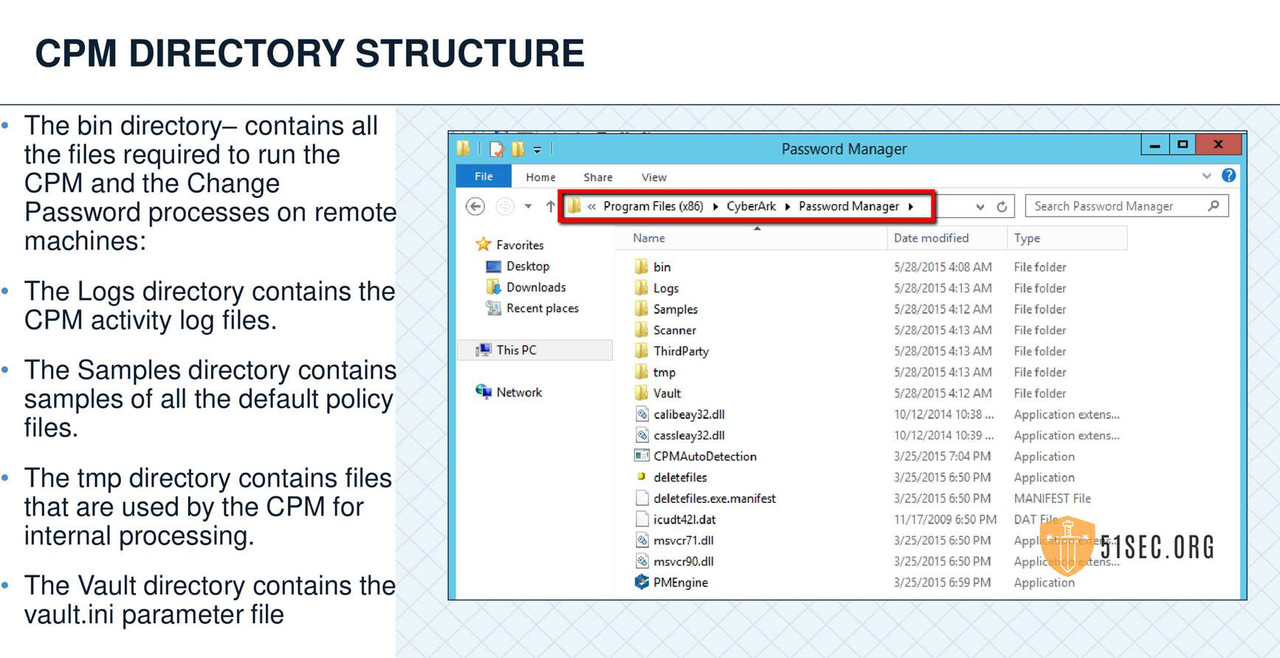
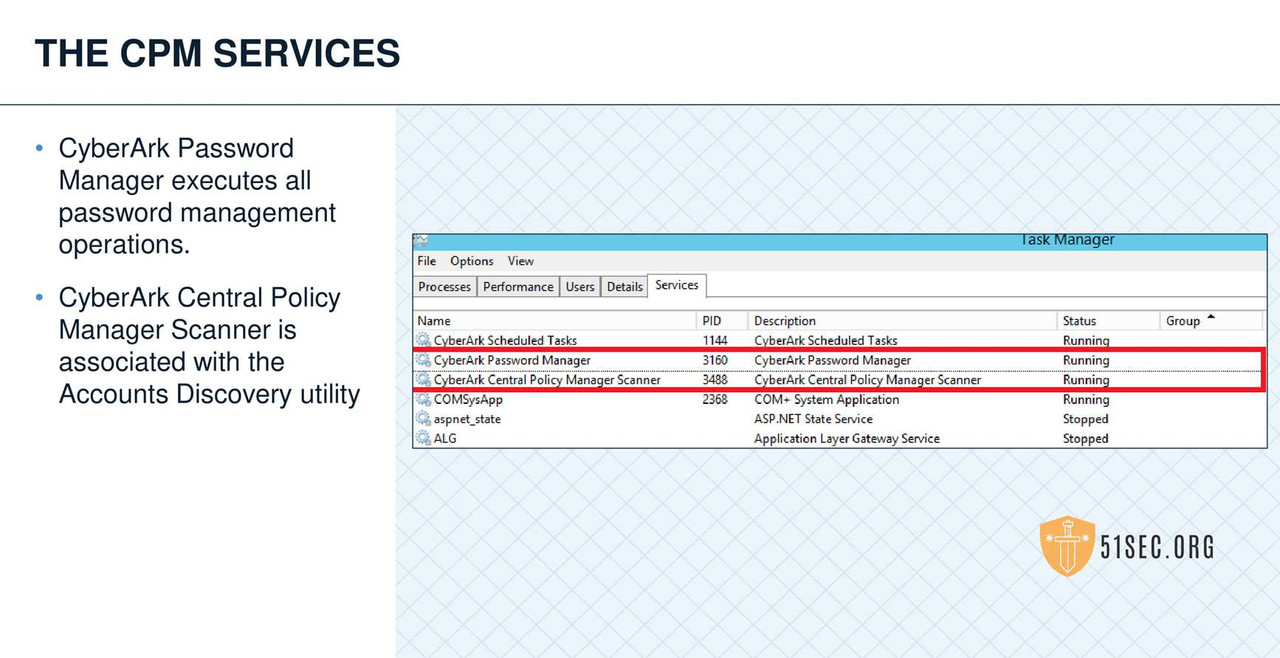
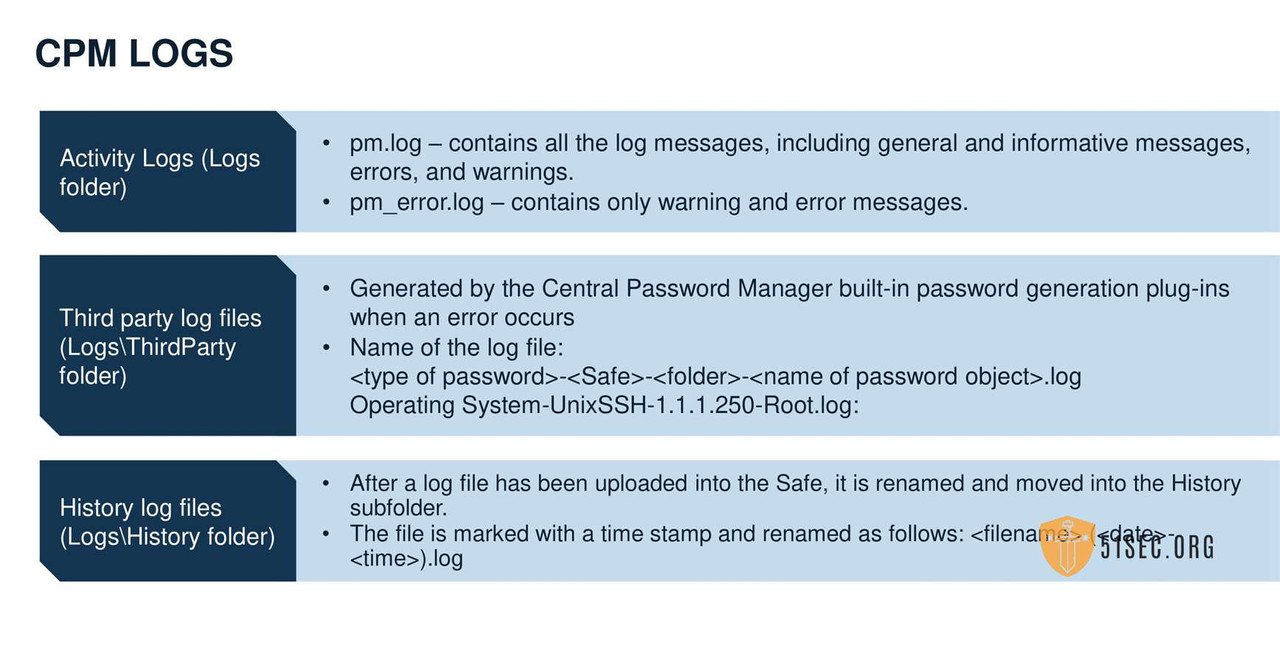
CPM VERIFY VAULT ENVIRONMENT
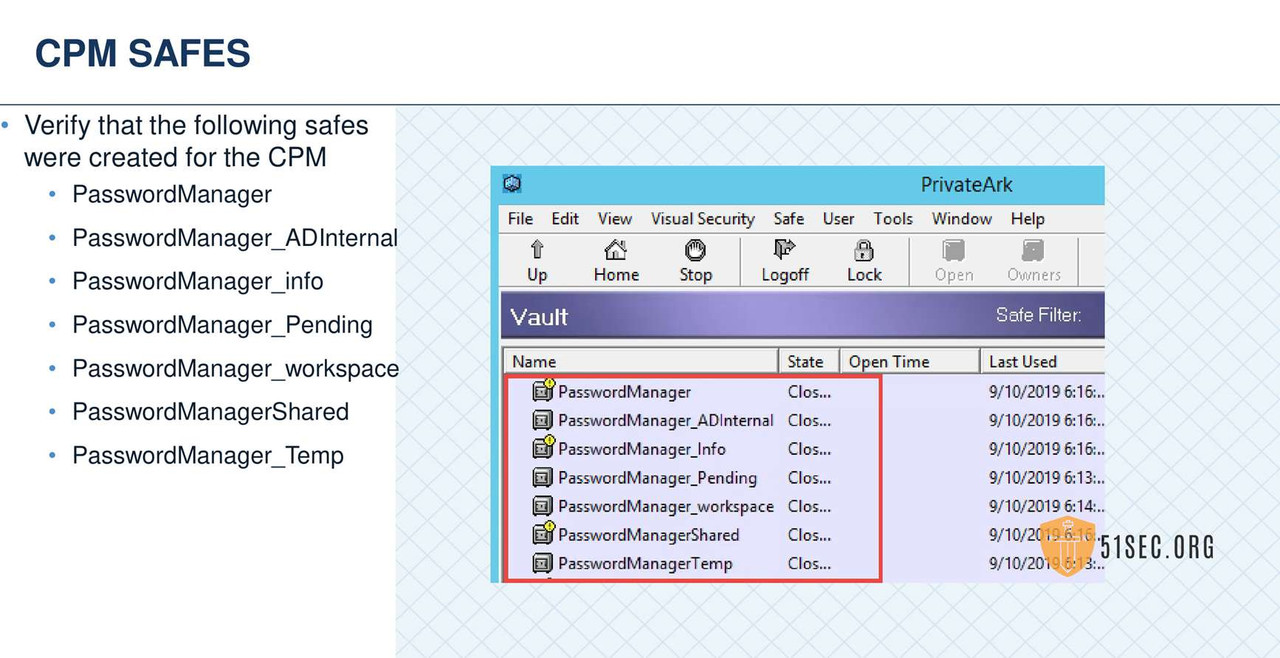
HARDENING THE CPM
HARDENING THE CYBERARK CPM AND PVWA SERVERS
The Hardening the CyberArk CPM and PVWA Servers webpage and document is designed to help you secure and harden the Windows servers that have CyberArk components installed on them
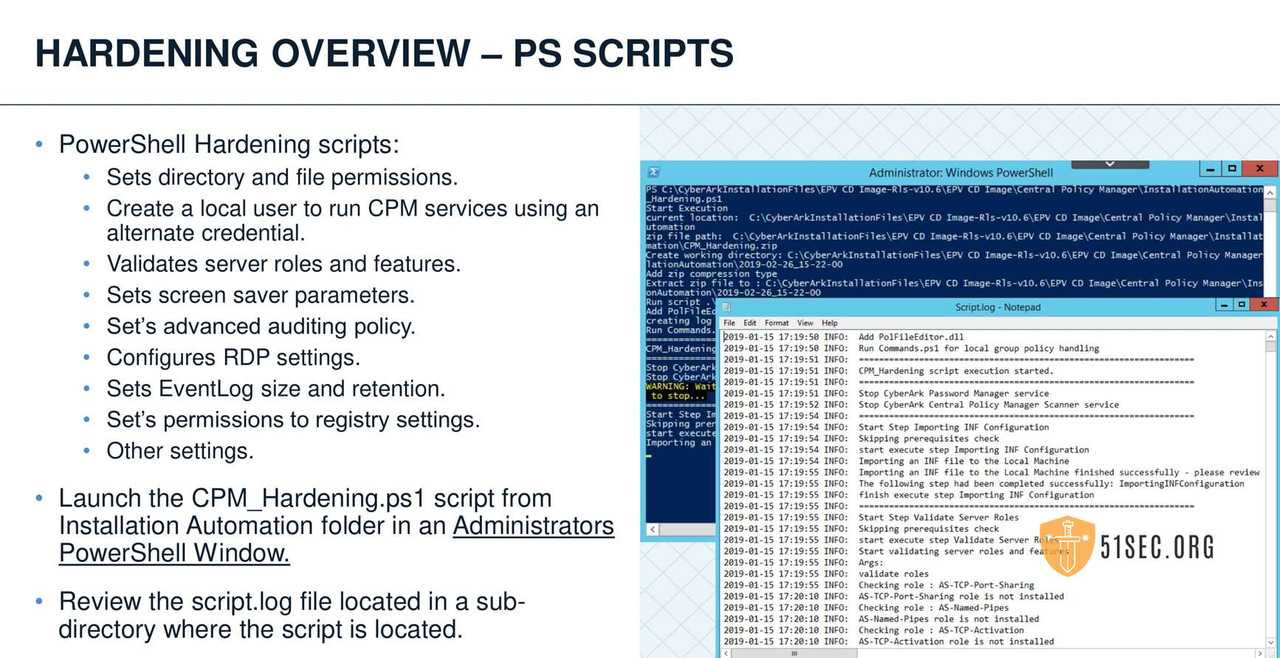
• CPM or PVWA hardening is accomplished via a combination of PowerShell scripts and GPO settings
• Instructions are provided for GPO deployment for in Domain environments and a manual procedure for out of domain environments
• PowerShell scripts are provided to compliment the deployment of the hardened configuration
• Both procedures must be completed to consider the hardening complete
HARDENING OVERVIEW GPO/INF
• In Domain Automatic Hardening via GPO
- • When the CPM and / or the PVWA server environments are part of Active Directory domain (' InDomain ’), a Group Policy Object can be applied to enforce security policies.
- • When the CPM and PVWA server environments are not a part of Active Directory domain ('Out of Domain'), the hardening procedure is applied via an INF file.
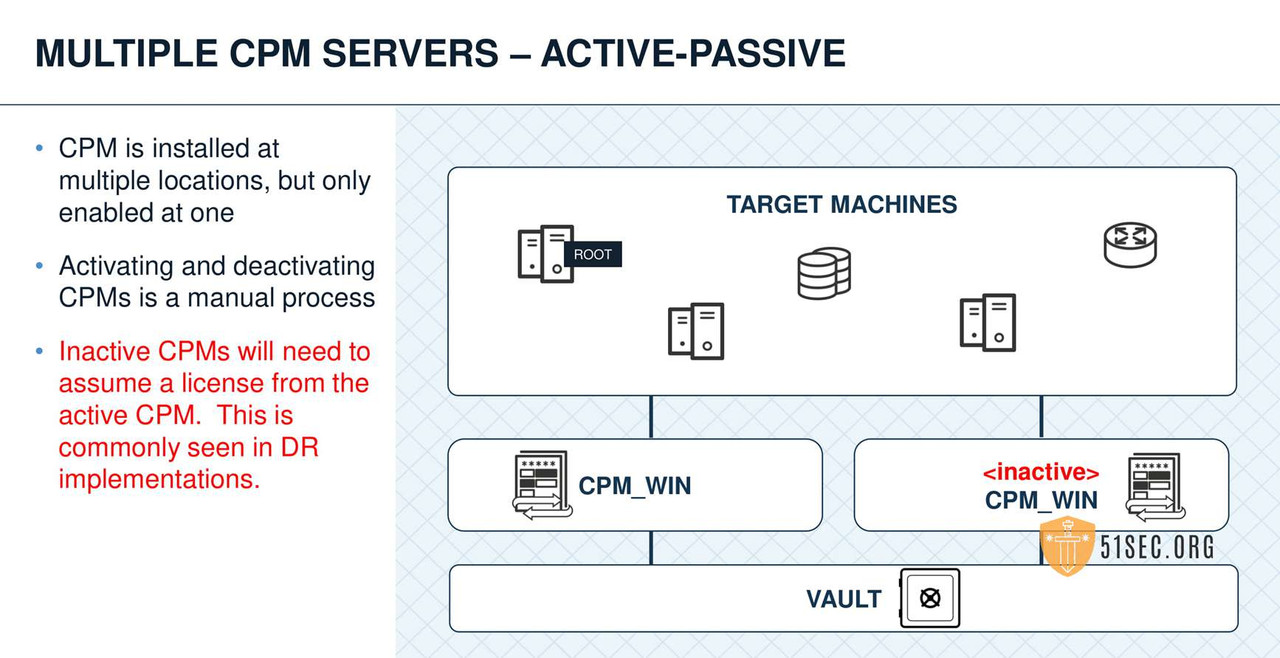
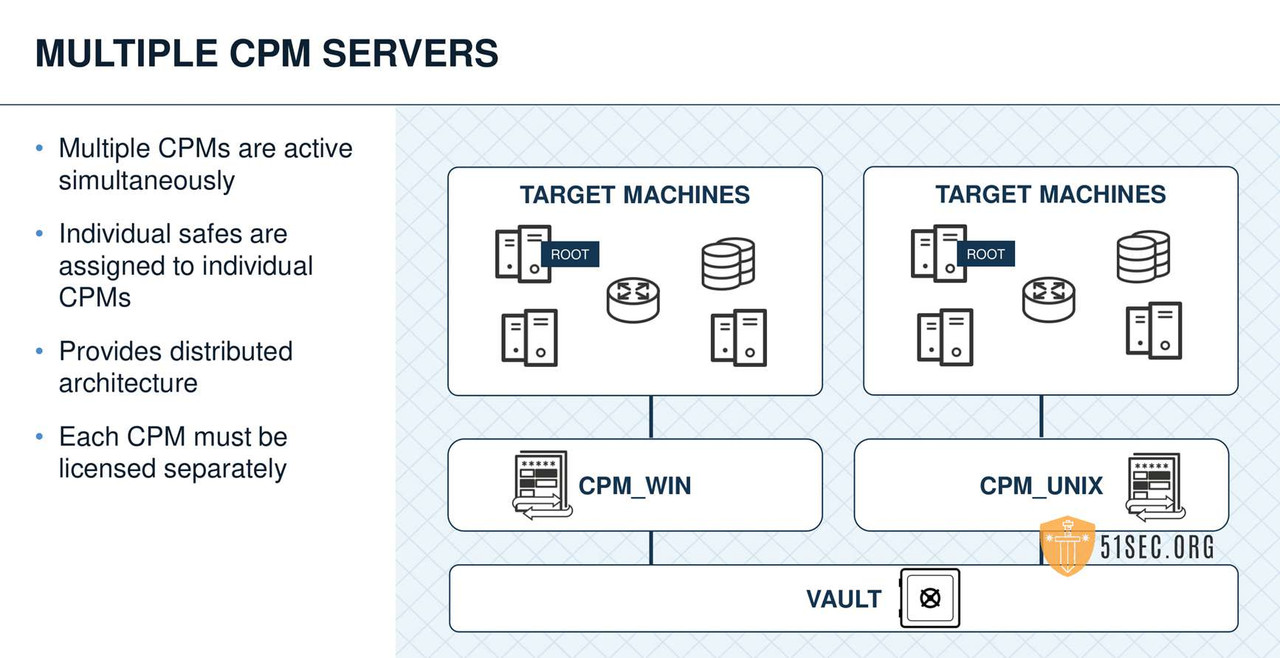
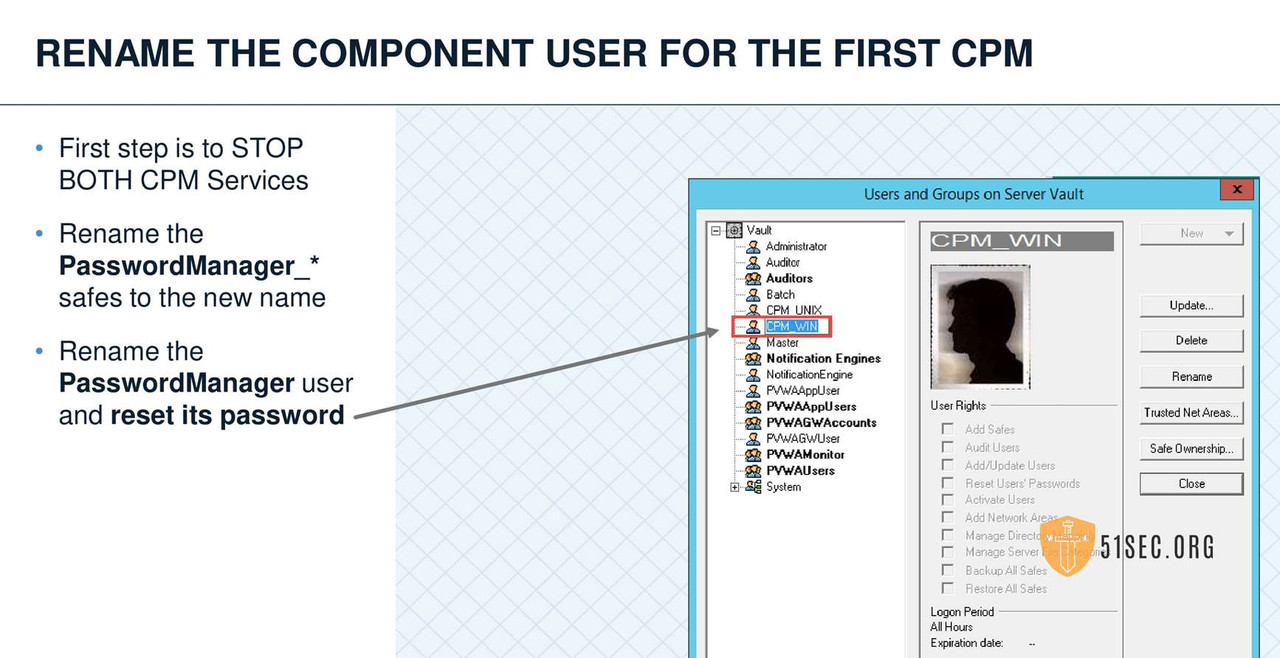
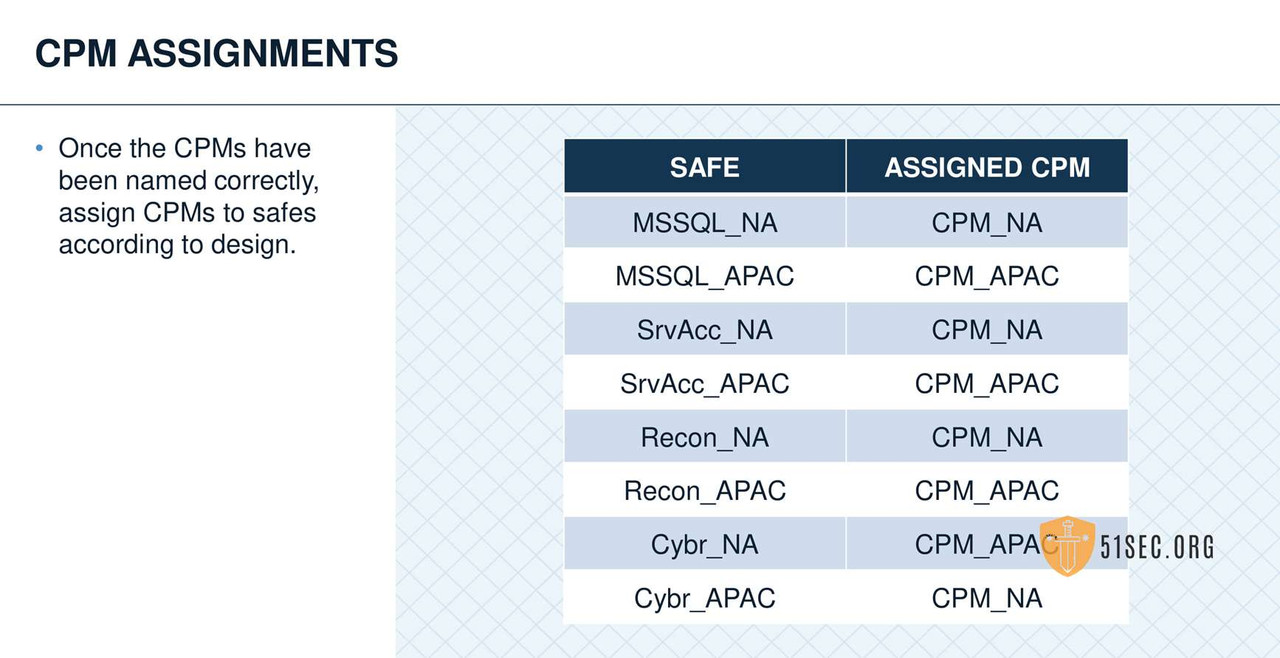
MULTIPLE CPMS
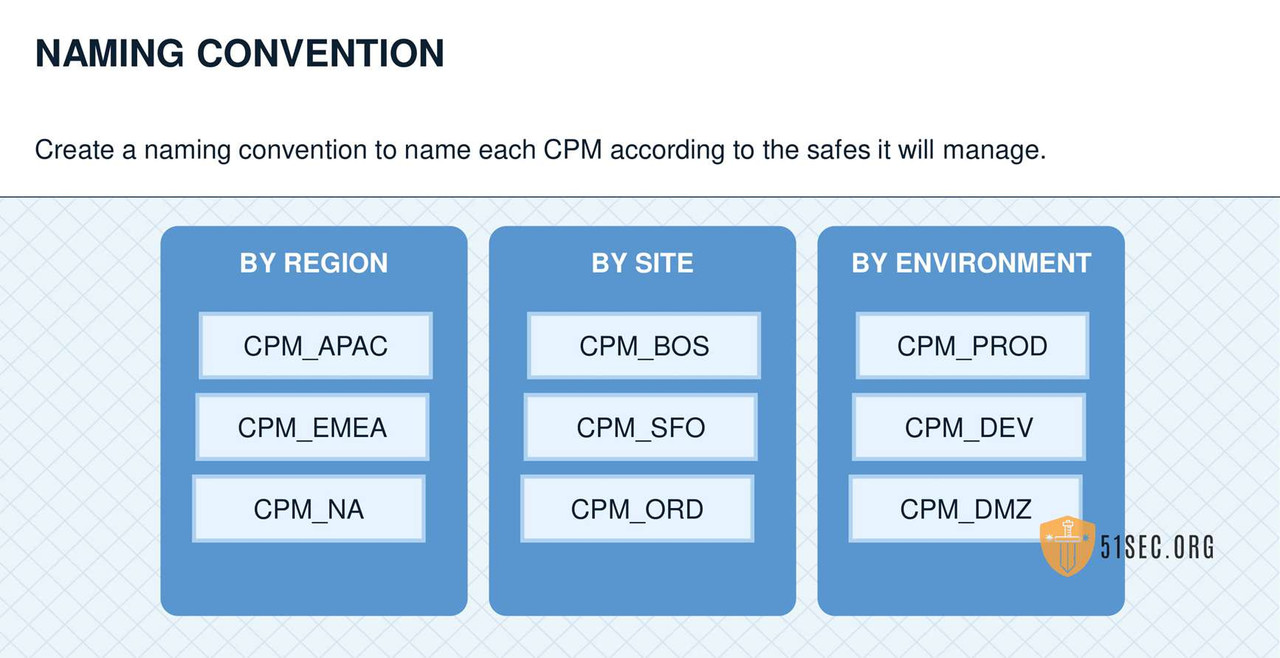
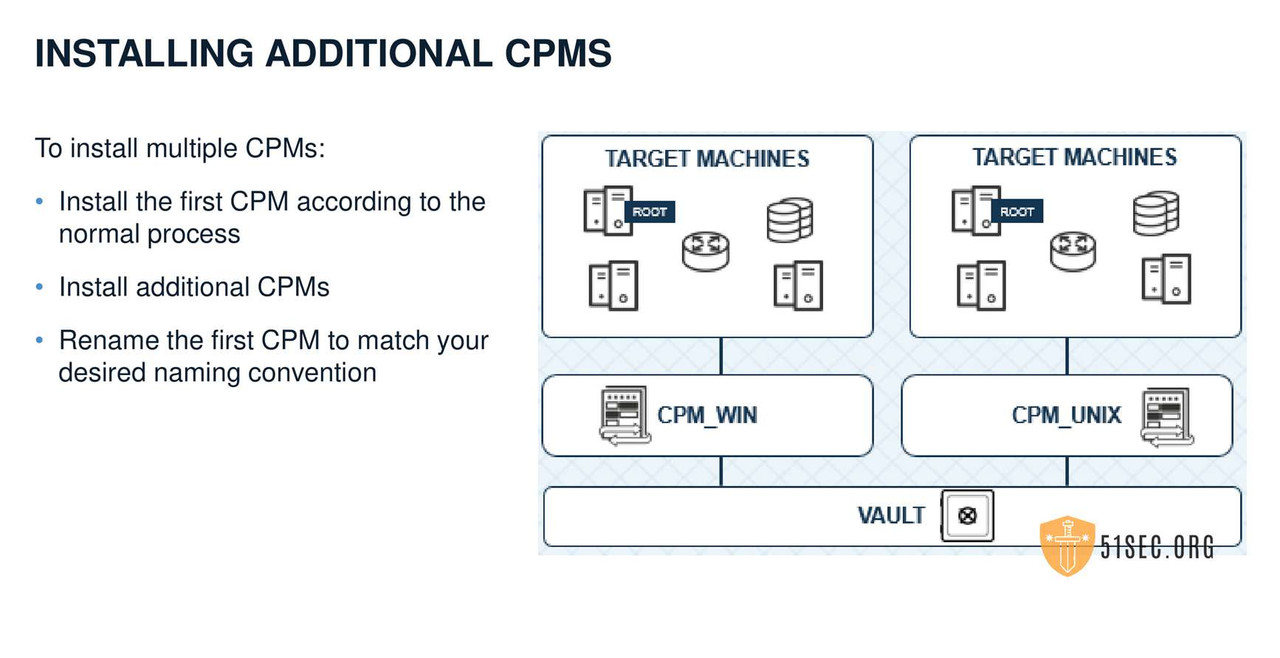
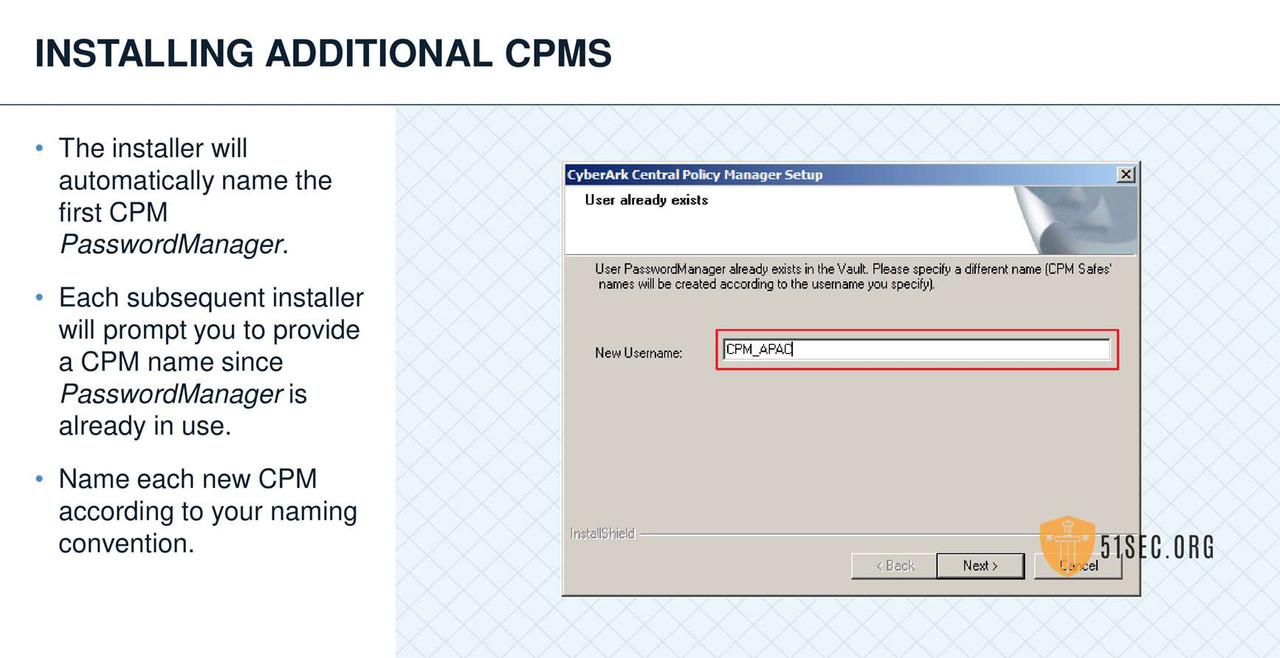
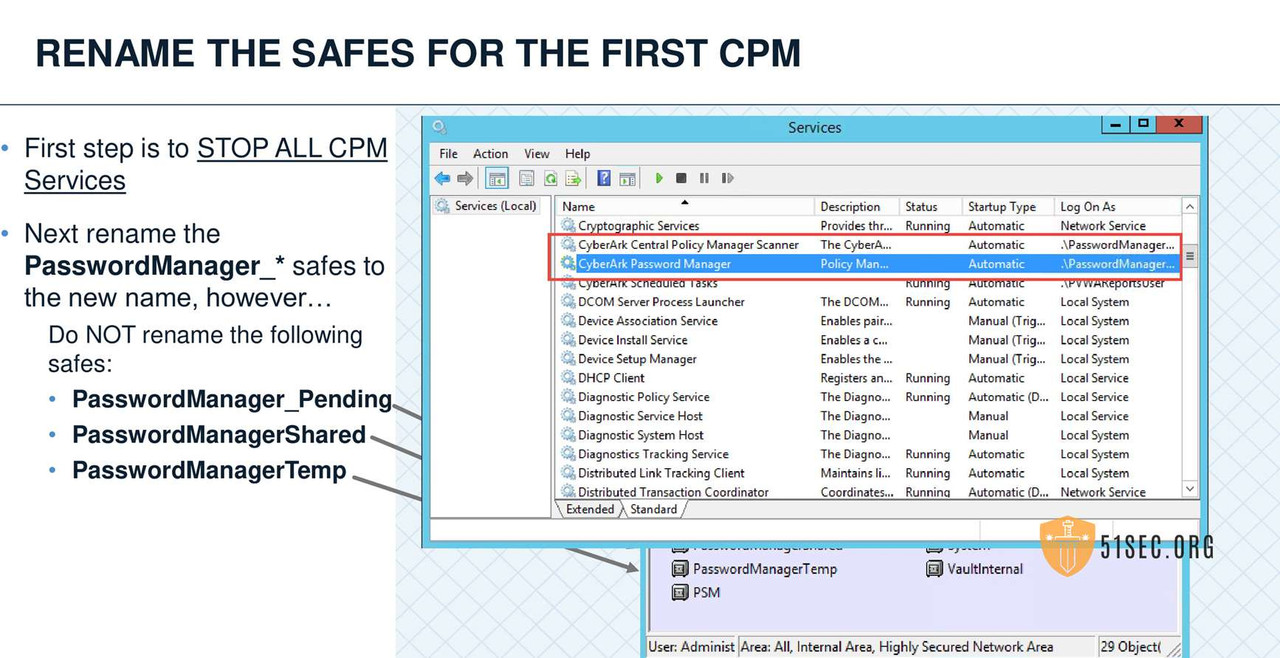



GENERAL CONFIGURATION AND RECOMMENDATIONS
GENERAL CONFIGURATION FOR ALL DEPLOYMENTS CONT.
• Restrict Network Protocols
- • Install only the required protocols and remove unnecessary ones. For example, only TCP/IP are necessary, and ensure that no additional protocols such as IPX or NetBEUI are allowed.
- • It is recommended to change the names of both the Administrator and the guest to names that will not testify about their permissions. It is also recommended to create a new locked and unprivileged Administrator user name as bait.
- • To minimize your attack surface, as a best practice, make sure that only the minimum roles and features that are required are defined on the CPM and PVWA server(s).
- • Remove all unnecessary roles and features.
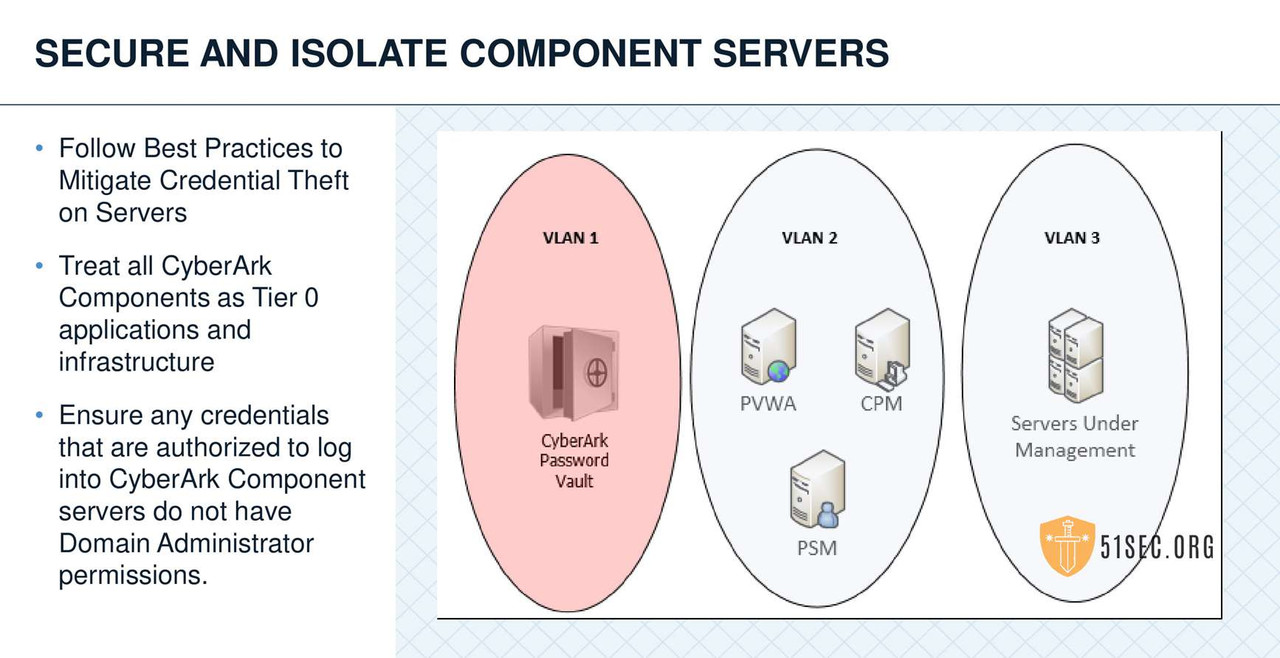
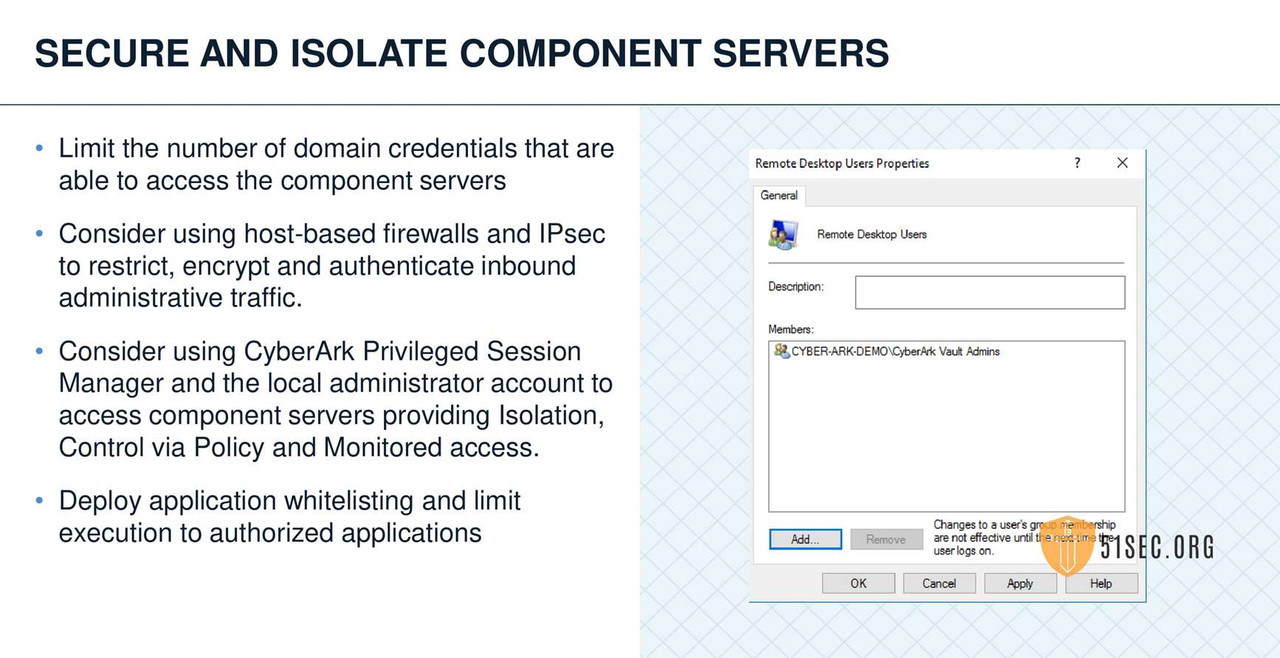
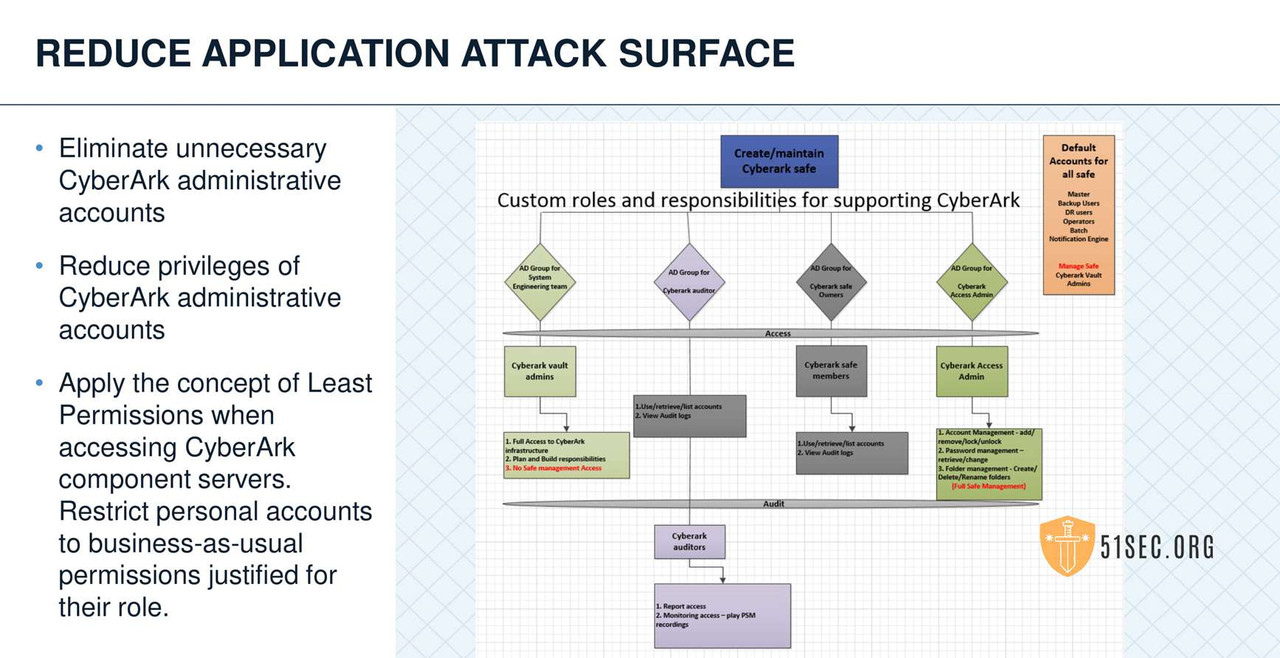
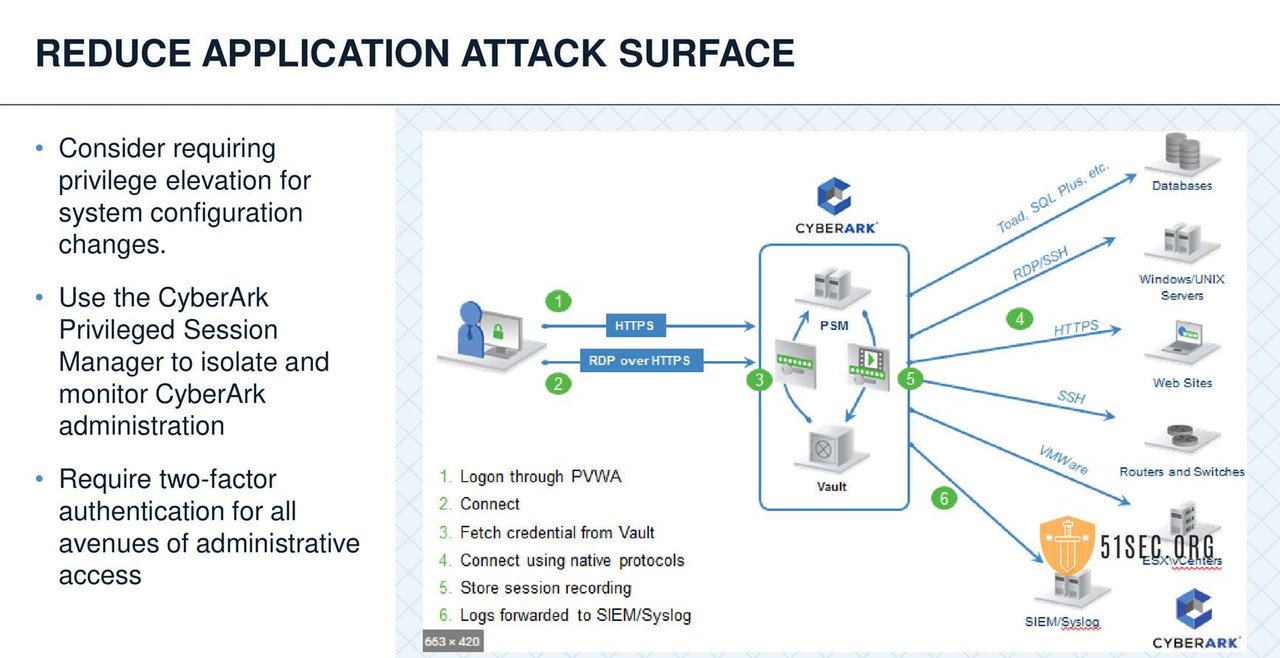
SUMMARY
This post covered:
• Installing the CPM and PVWA
• Configuring the CPM and PVWA
• The CPM and PVWA Server Environment
• The CPM and PVWA Vault Environment
• Securing the CPM and PVWA







No comments:
Post a Comment