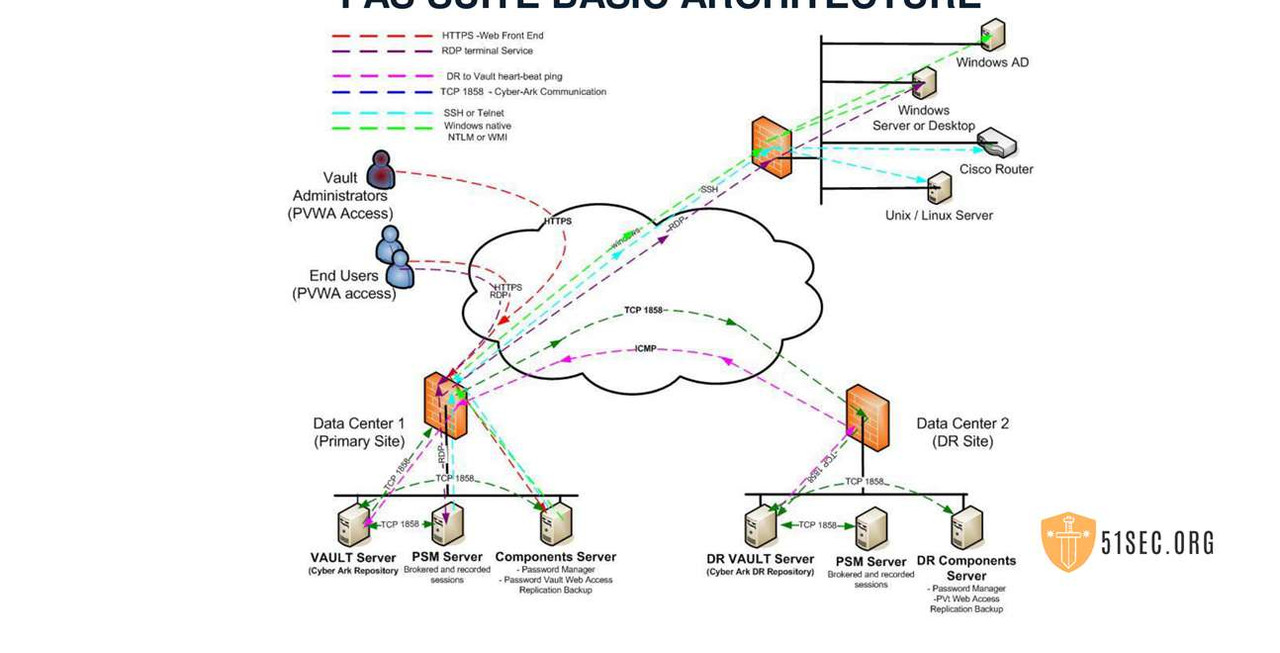
PAS Suite Basic Architecture
Related Posts:
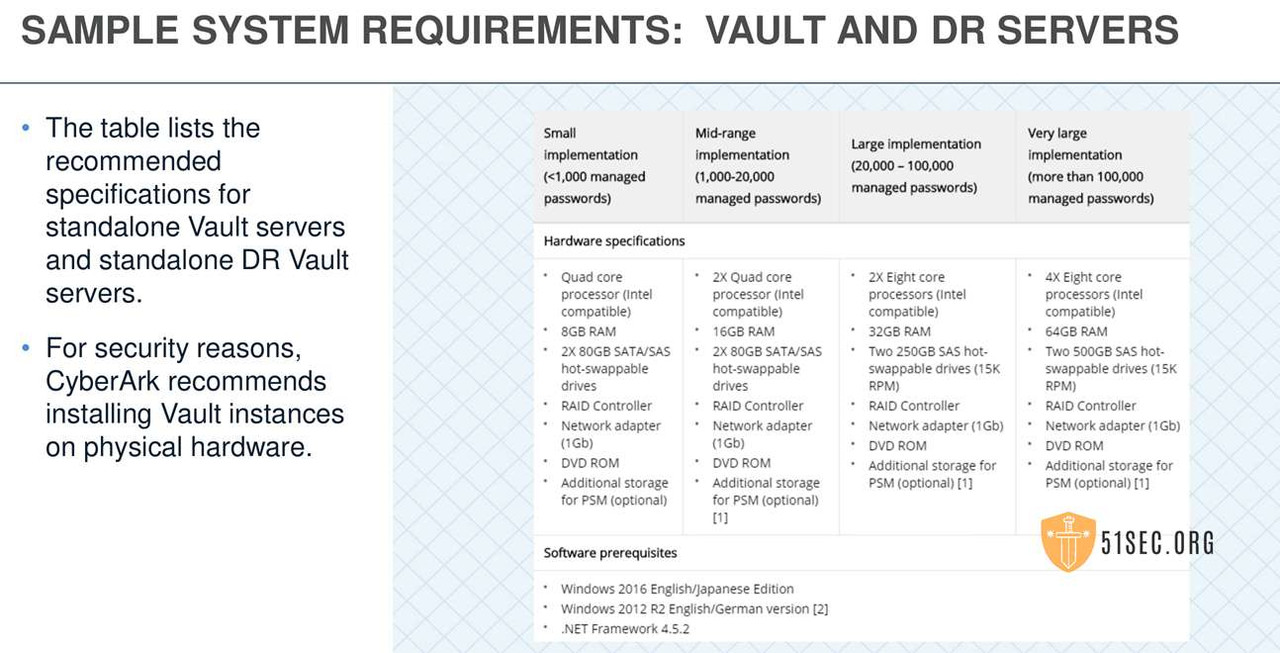
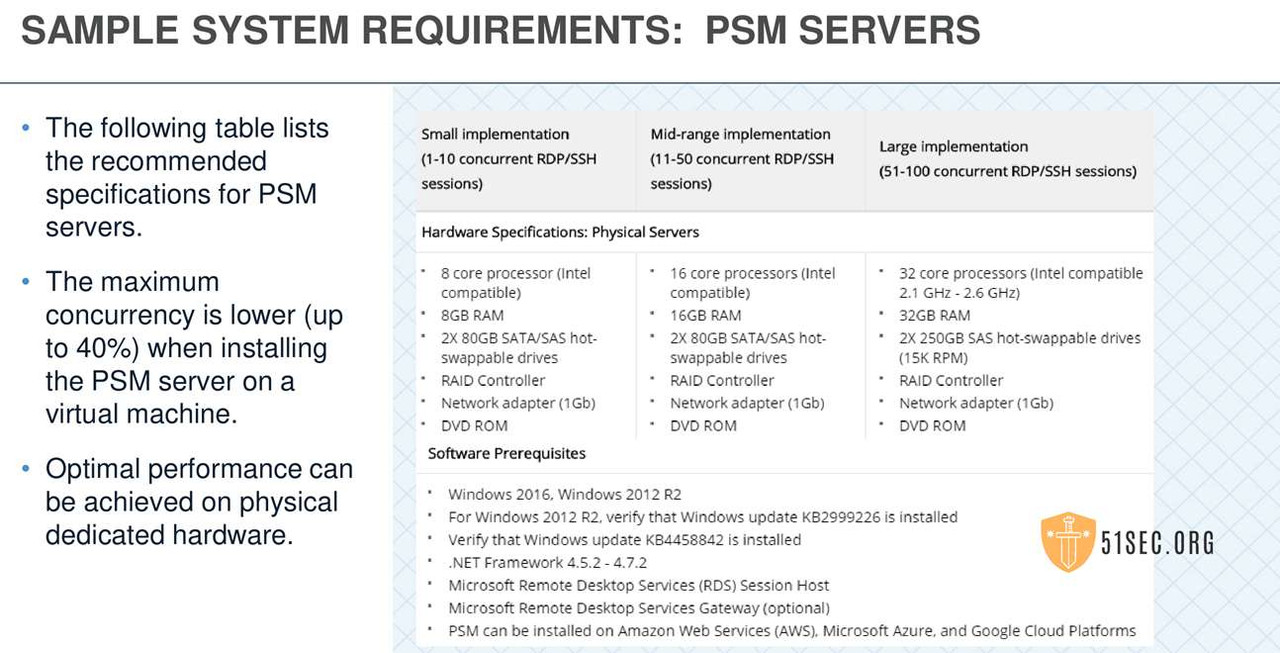
PRIVILEGED ACCESS SECURITY SYSTEM REQUIREMENTS
VAULT SERVERS SETUP
Review the document “Digital Vault Security Standard” at https://docs.cyberark.com/
• The Digital Vault should be installed on a dedicated physical machine (recommended) from original
Microsoft installation media.
• Built from the original Microsoft installation media.
• No third party software, such as anti virus or remote management solutions.
• The Digital Vault Server shall not be a member of any enterprise domain.
• Isolate the Digital Vault Server, in a secure VLAN.
PRIVILEGED ACCESS SECURITY INTEGRATIONS
LDAP INTEGRATION
• Create an LDAP Bind account with READ ONLY access to the directory.
- • Have the User Name, Password, and DN available
- • Interactive logon is not required.
• Create three LDAP groups for granting access to the vault.
- • Cyberark Administrators
- • Cyberark Auditors
- • Cyberark Users
• In support of LDAP/S, install the Root Public Key certificate for the Certificate Authority that issued the certificate to the directory servers, on the Vault Servers.
- • Update hosts file on the vault servers with directory server names.
EMAIL INTEGRATION
• Have the IP address of all SMTP Gateways Available.
• Ensure that any necessary firewall rules or ACLs allow communications from the Vault Servers to the SMTP Gateway.
• The Vault Server must be authorized to send SMTP messages to the SMTP Gateway.
• Schedule SMTP gateway administrator to be available during the integration.
• Please refer to the “Standard Ports and Protocols” at https://docs.cyberark.com/
SNMP MONITORING INTEGRATION
• Have IP Addresses of all servers that can accept SNMP traps available.
• Upload SNMP v1 or v2 MIB files.
• Have Community String available.
• Have a resource from the team responsible for SNMP servers available.
SIEM MONITORING INTEGRATION
• Find out the relevant SIEM vendor for the organization in question.
• Have IP addresses of all servers that can accept SYSLOG information available.
• Have a resource from the team responsible for SYSLOG servers available.
RADIUS OR RSA INTEGRATION
• Have the IP addresses of all RSA or RADIUS servers available.
• Create host entries in RSA or RADIUS for all Vault servers.
• Have the “secret” that was used during host entry creation available.
NTP INTEGRATION
• Have the IP addresses of all NTP servers available.
SAMPLE AGENDA AND CONSIDERATIONS FOR IMPLEMENTATION
SAMPLE AGENDA FOR “GETTING STARTED” 4 DAY ENGAGEMENT
• Onsite Day 1 Install and perform initial configuration of the Production and DR Vaults including
advanced Vault integration such as SNMP, SMTP, SYSLOG and any others the were agreed upon.
• Onsite Day 2 Install and perform initial configuration of the Central Policy Manager, Password
Vault Web Access 1 and 2, Privileged Session Manager, Secure Replication Utility and the Private
Ark Client.
• Onsite Day 3 Perform advanced configuration for the CPM, PVWAs and PSM. Test CPM
management on 3 5 types of the out of the box plug ins. Test PSM workflows on 3 5 types of the
out of the box connectors.
• Onsite Day 4 Troubleshoot any issues discovered during the CPM testing and PSM workflows.
Perform overview session with administrators. Go over and assist in documenting the Master Policy,
Access Control Model data and permission structures. Set up and go over support access and
procedures.
• This agenda is intended as a general example.
OTHER CONSIDERATIONS
• Have test accounts available for CPM testing
• Windows local administrator
• Windows Domain Account
• Linux SSH or Cisco
• Other relevant accounts
• Make sure firewalls will not interfere with communication between Cyberark servers or with clients.
• Get an estimate of how many accounts will be managed and what type they might be. (Windows domain or enterprise admin, Unix root, Oracle SYS,etc
SAMPLE CONTACT INFO REQUEST
Could I please have the following items so we can effectively communicate about our engagement?
Contact Name:
Contact Phone
Contact Email:
Contact Site Location (if onsite):
SUMMARY
This post covered:
• Reviewed general system hardware requirements.
• Reviewed integration requirements.
• Reviewed a sample 4 day agenda.








No comments:
Post a Comment