Objectives:
By the end of this post you will be able to:• Describe the CyberArk components that comprise the Enterprise Password Vault and Privileged
Session Management solutions.
• Describe the Architecture of the EPV and PSM solutions.
• Describe the key recommendations for protecting the CyberArk environment.
Related Posts:
Review
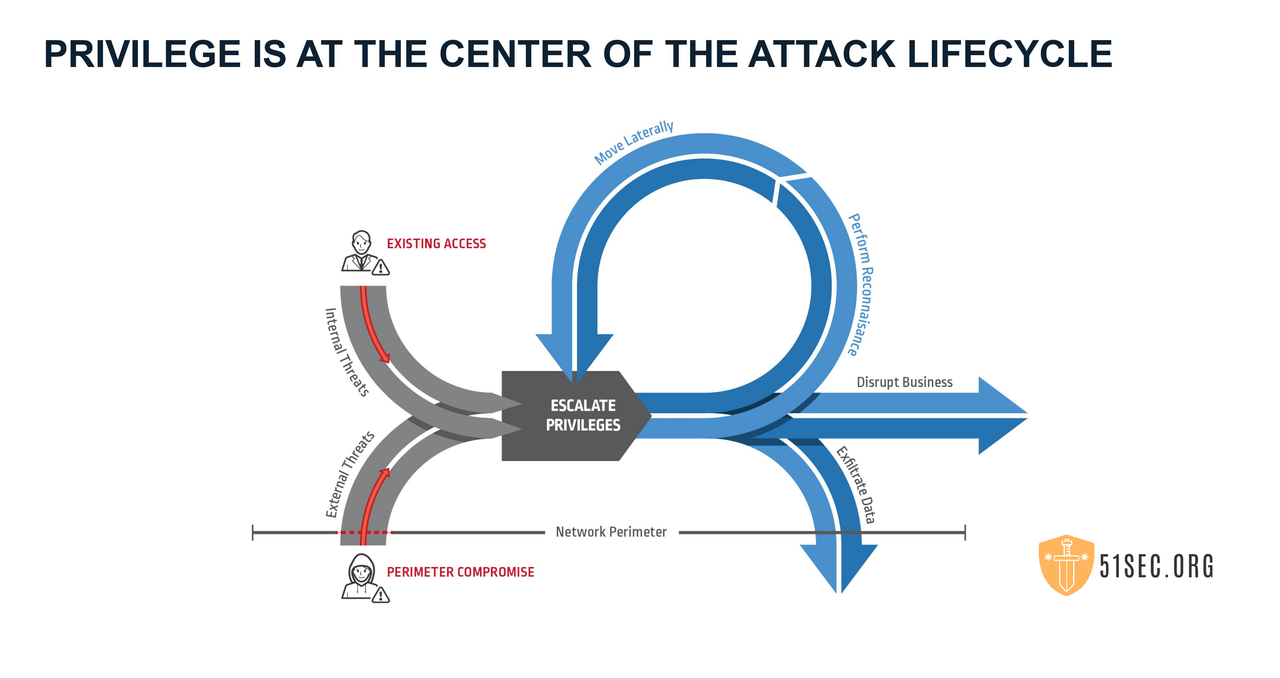
PAS solution can block the threats before hackers escalate privileges , even they did preform reconnaissance.
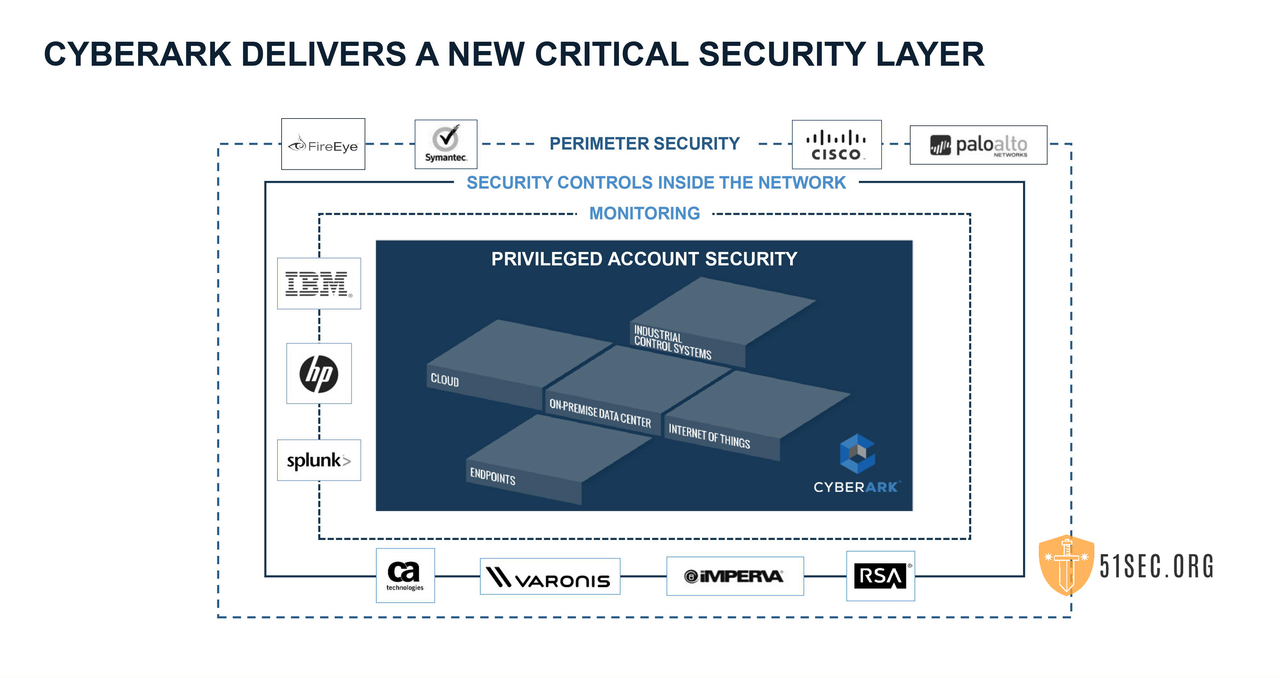
Multilayered Security:
- Perimeter Security (Fireeye, Symantec, Cisco, Palo Alto, Check Point, etc)
- Security Controls inside the network ( CA Technology, Varonis, iMPERVA, RSA)
- Monitoring ( IBM Qradar, HP ArcSight, Splunk)
- Privileged Account Security
- Industrial Control System
- Cloud
- On Premise Data Center
- Internet of Things
- EndPoints
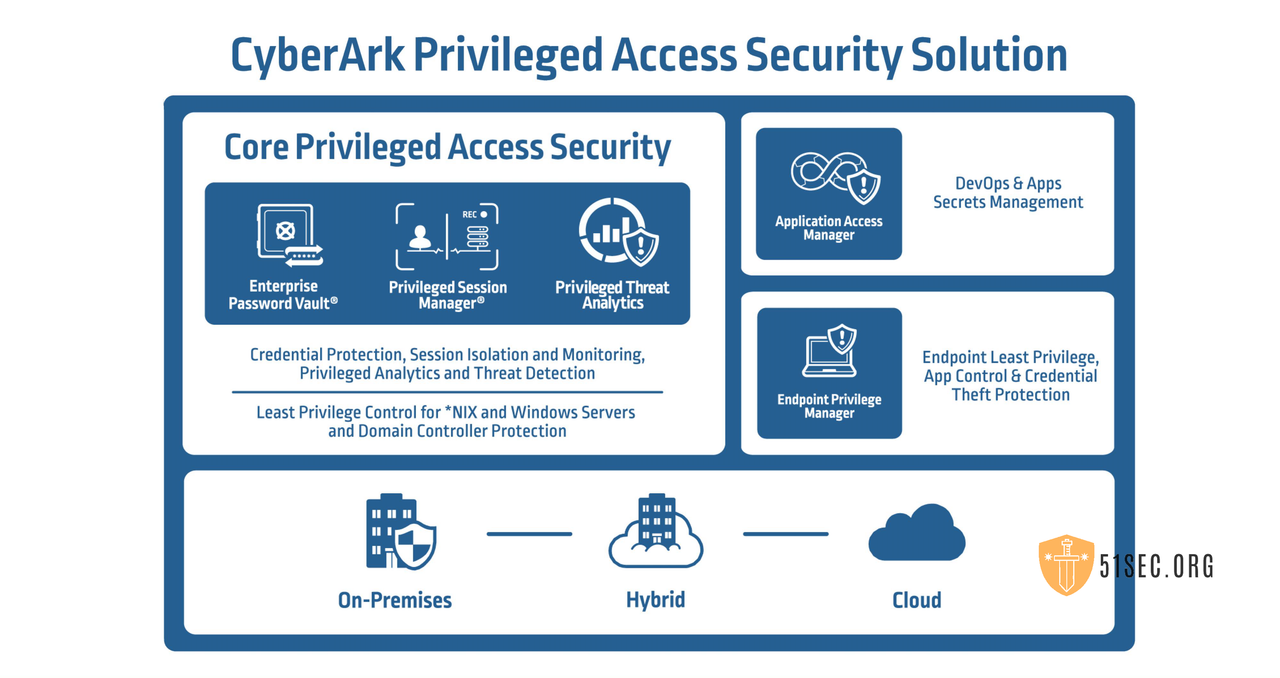
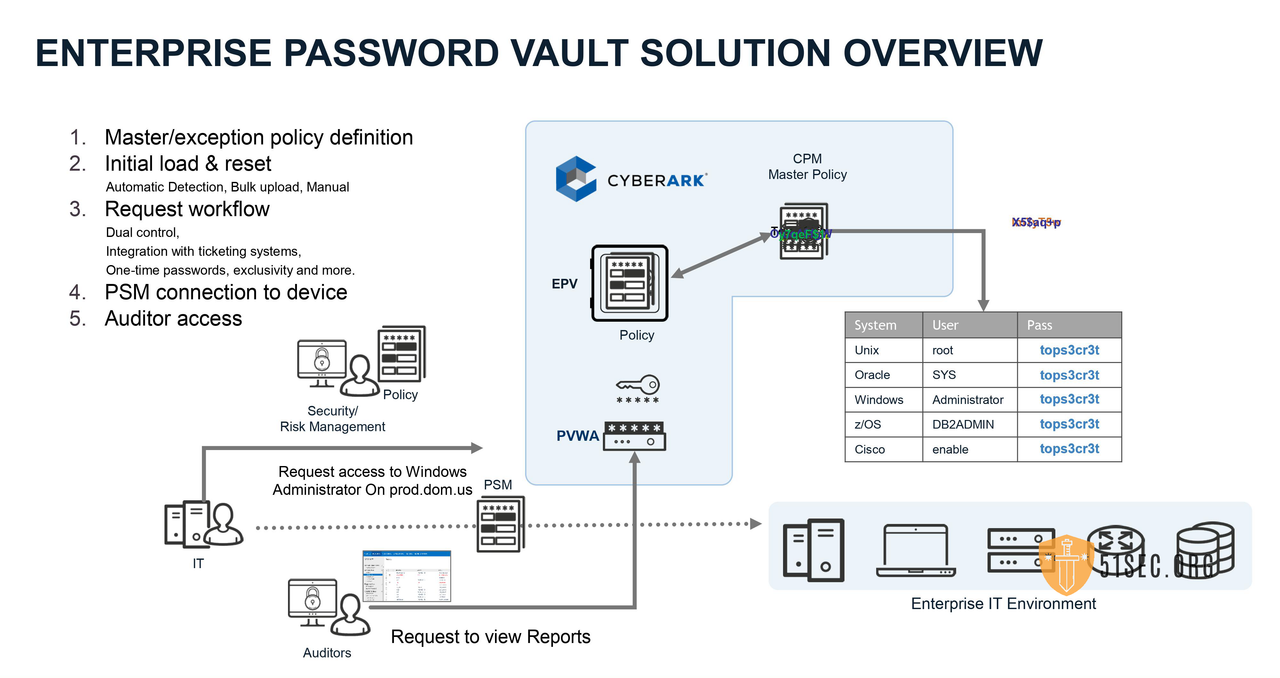
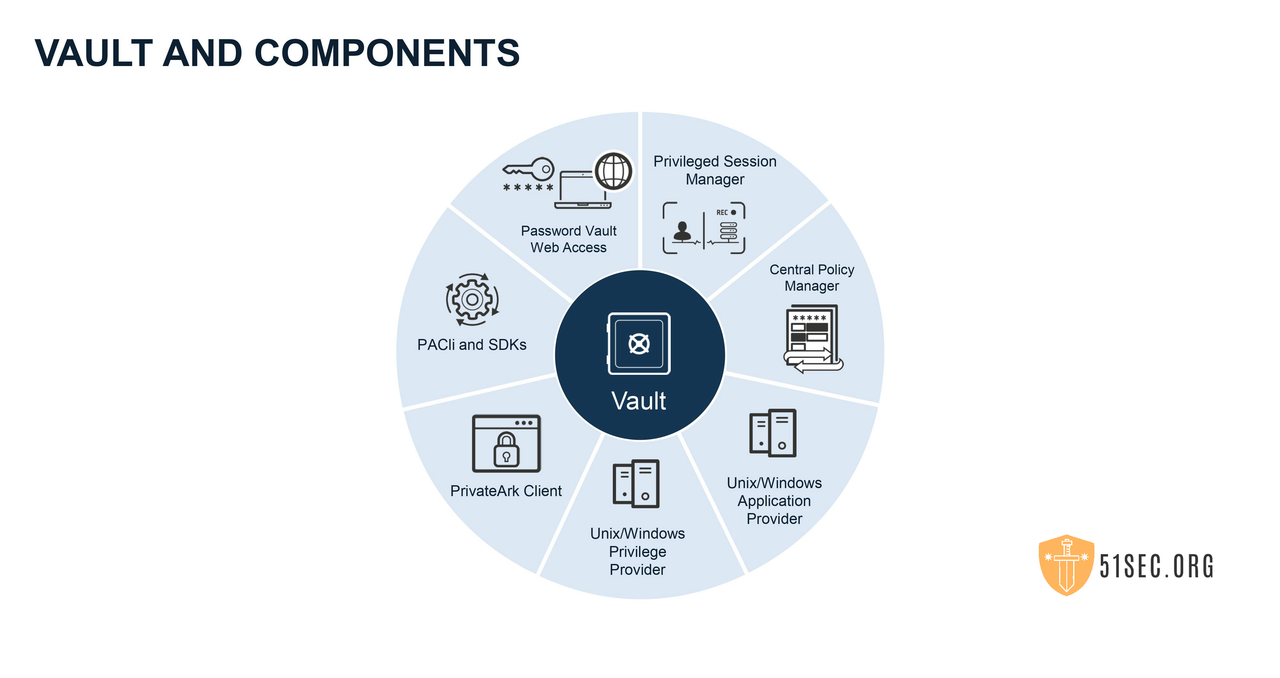
EPV = Digital Vault + PVWA + CPM
There is no PSM in the EPV.
Enterprise Password Vault
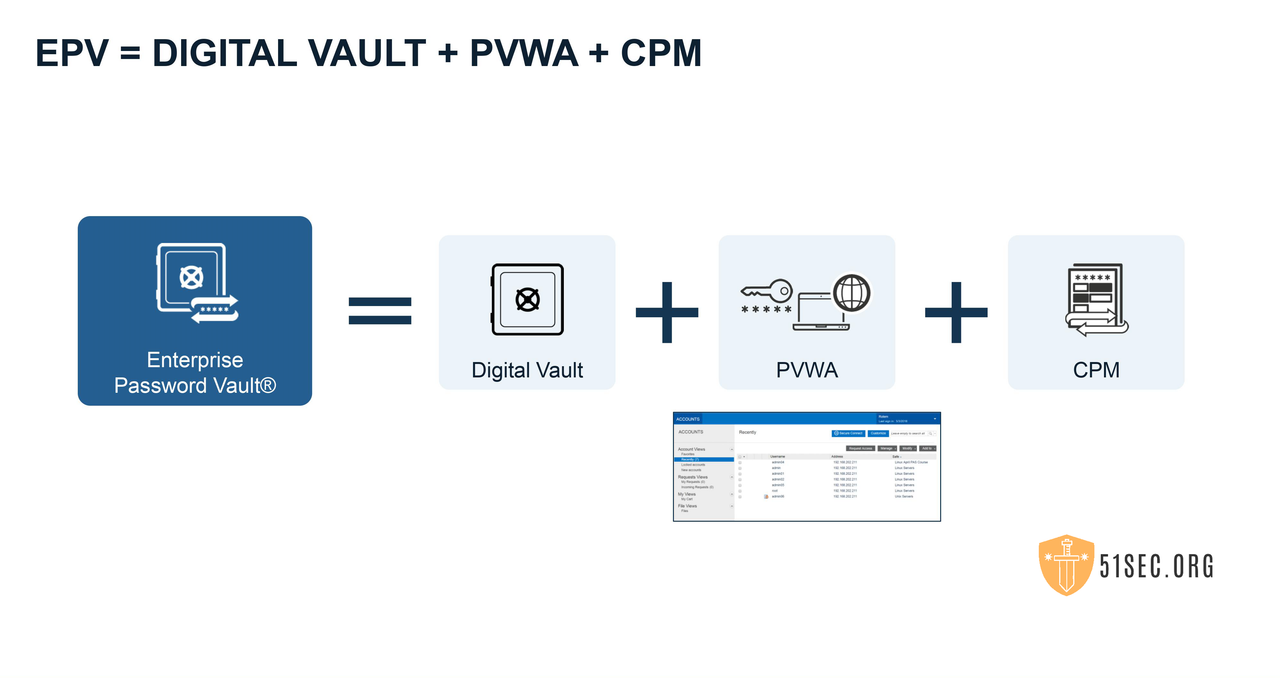
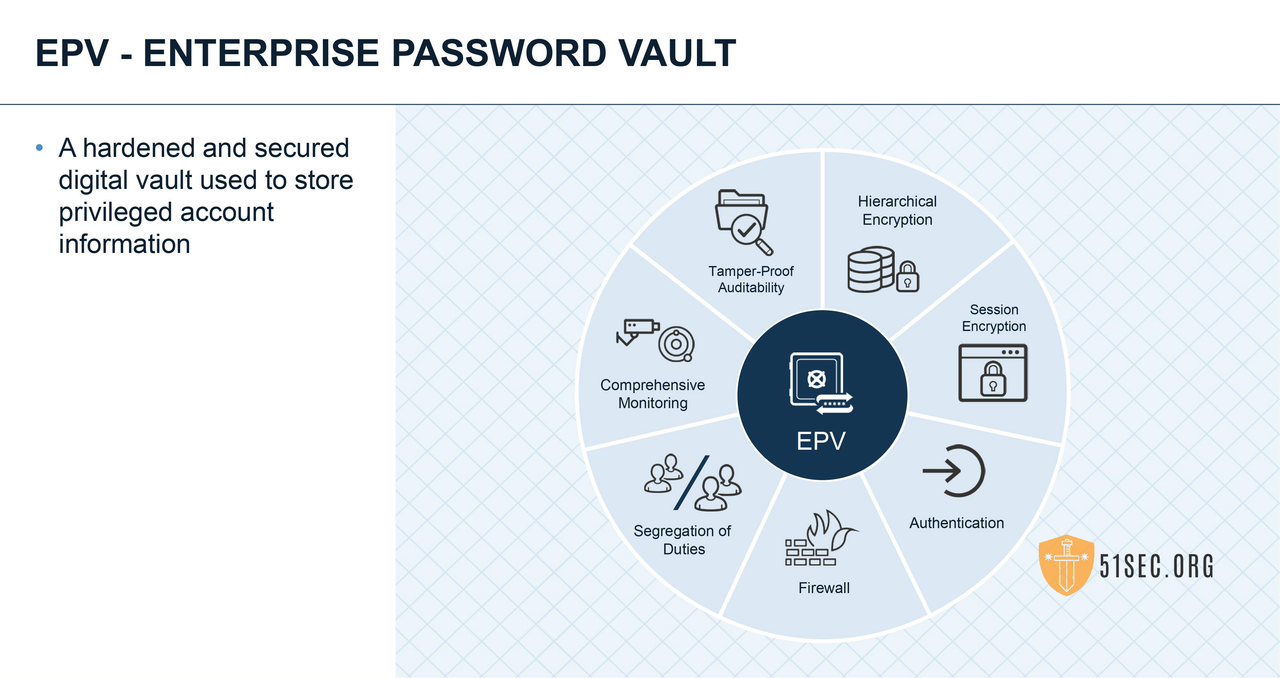
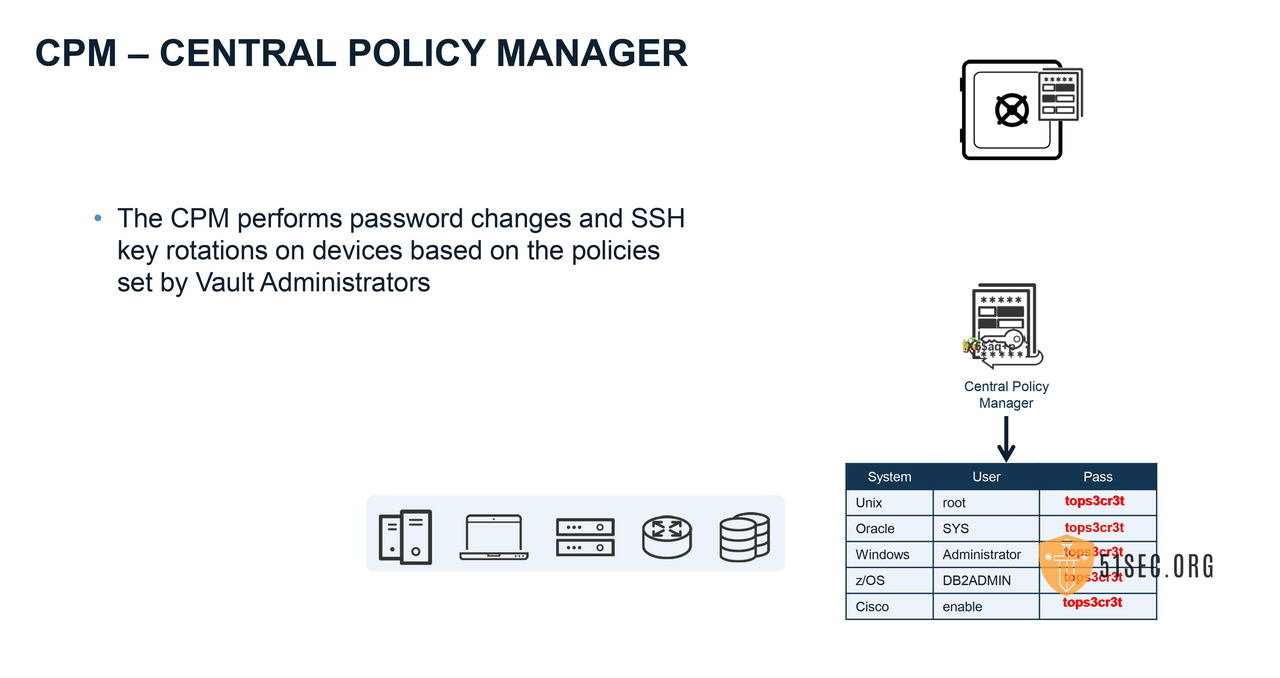
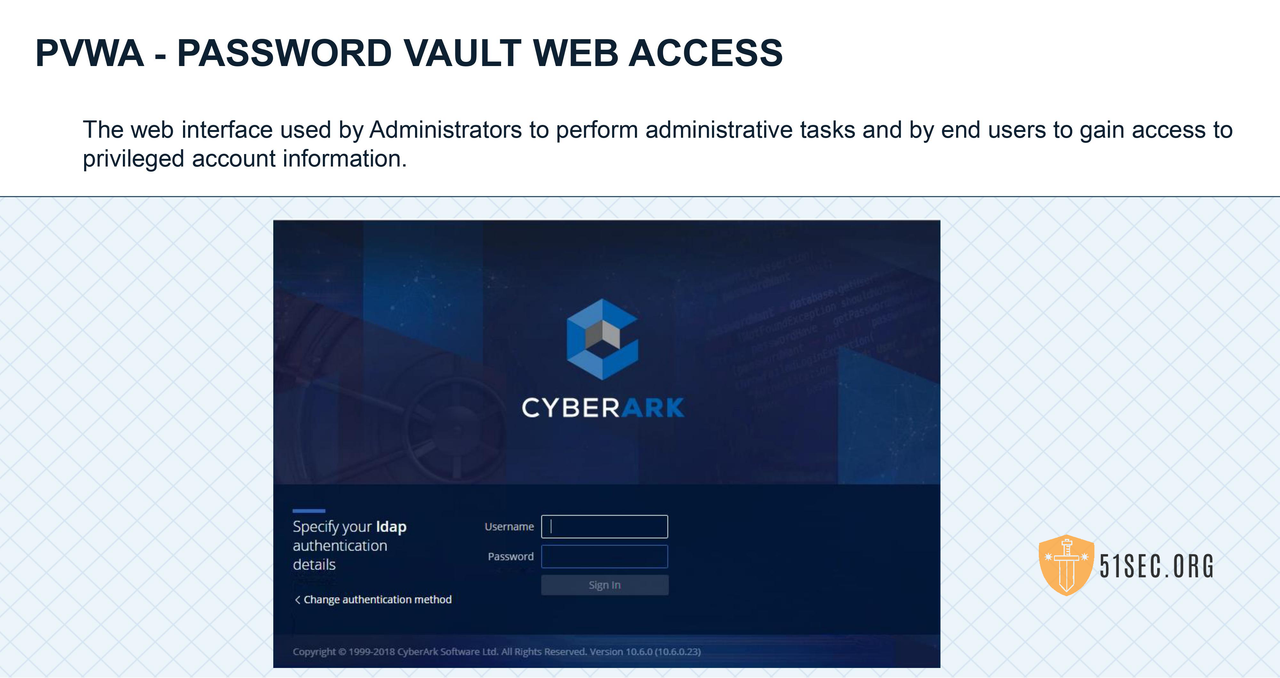
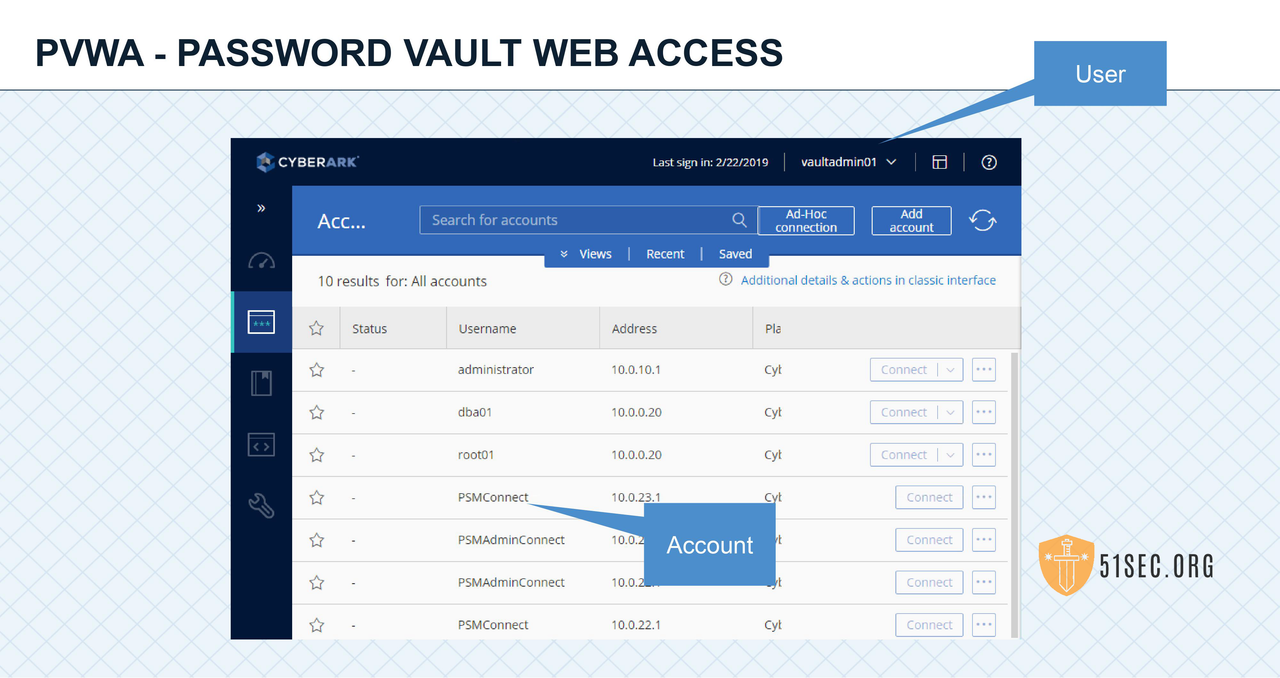
In CyberArk technical terms, there is a big difference between User and Account.
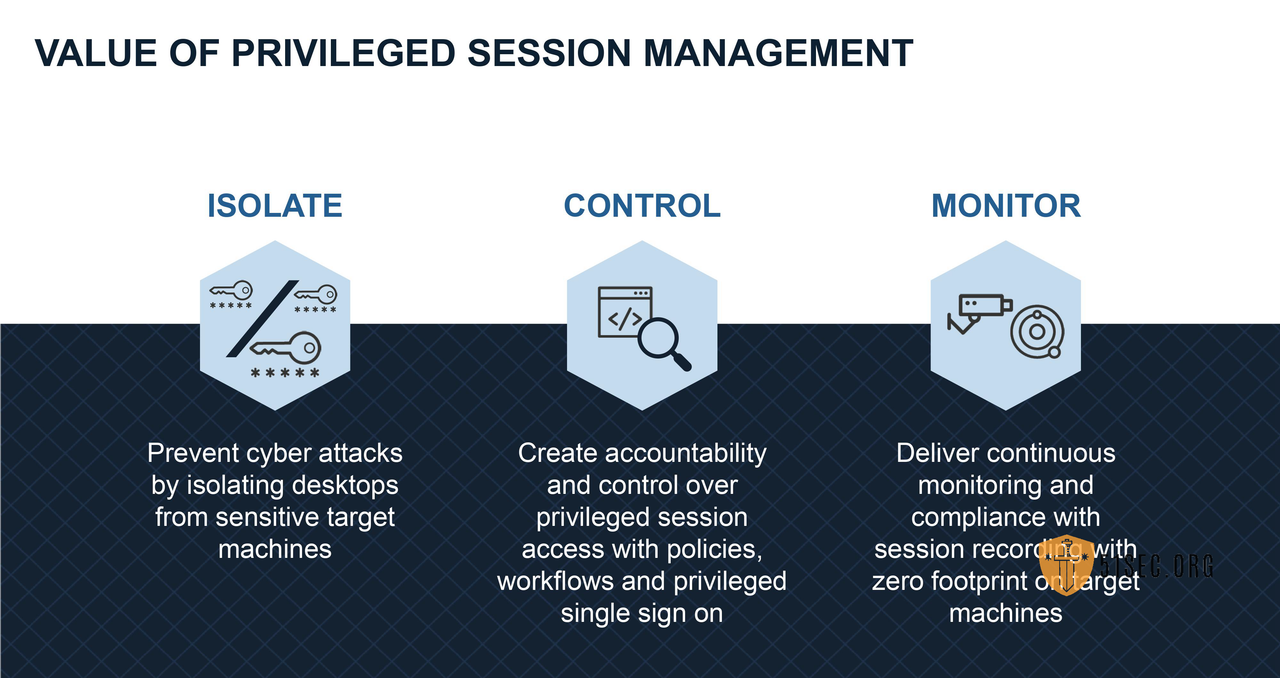
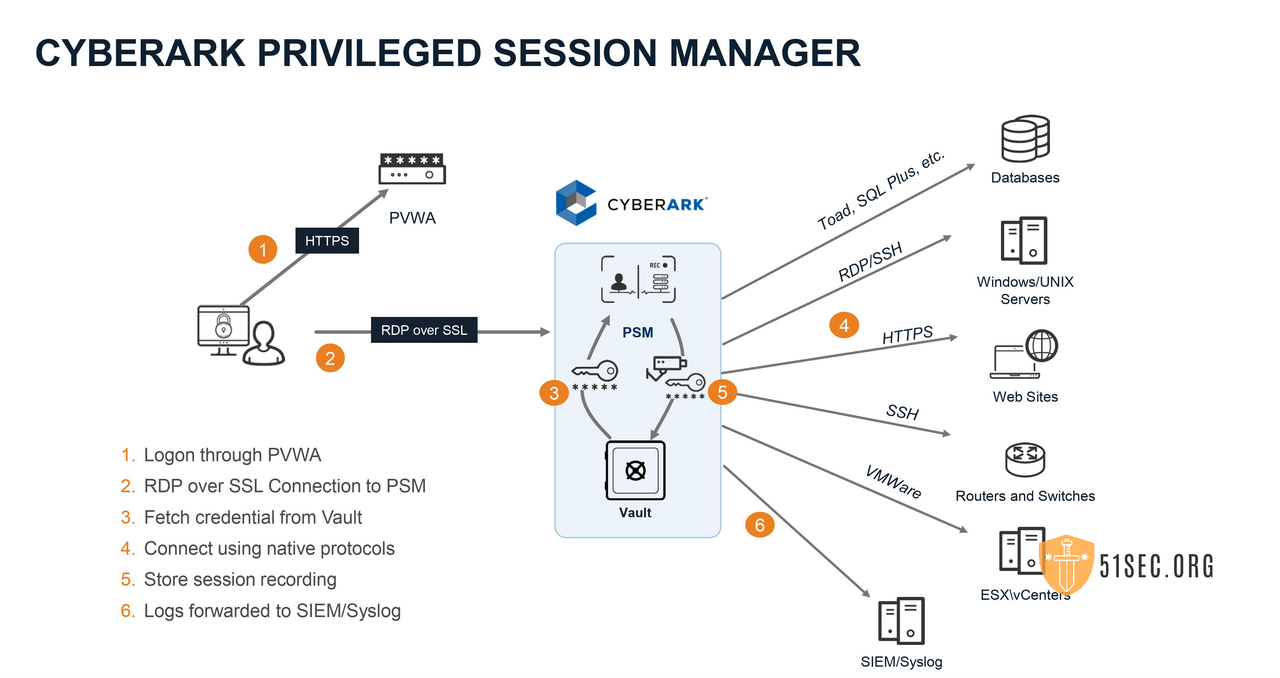
Privileged Session Management (PSM)
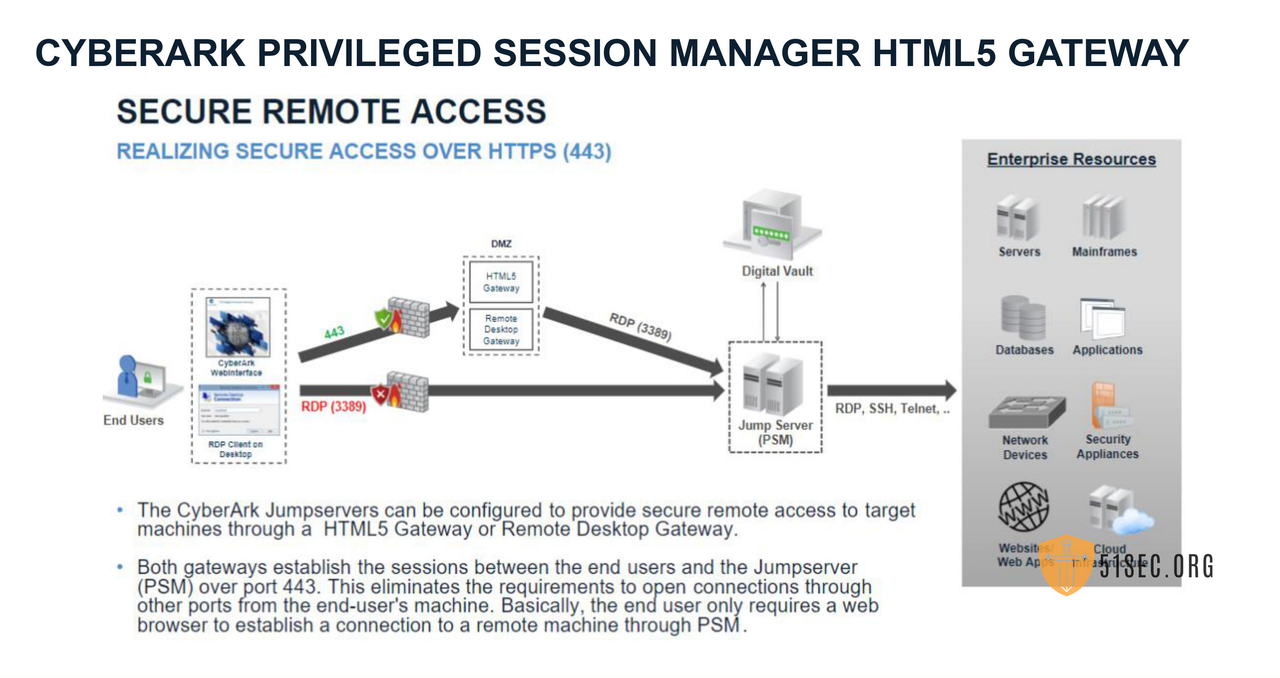
High Level Systems Design
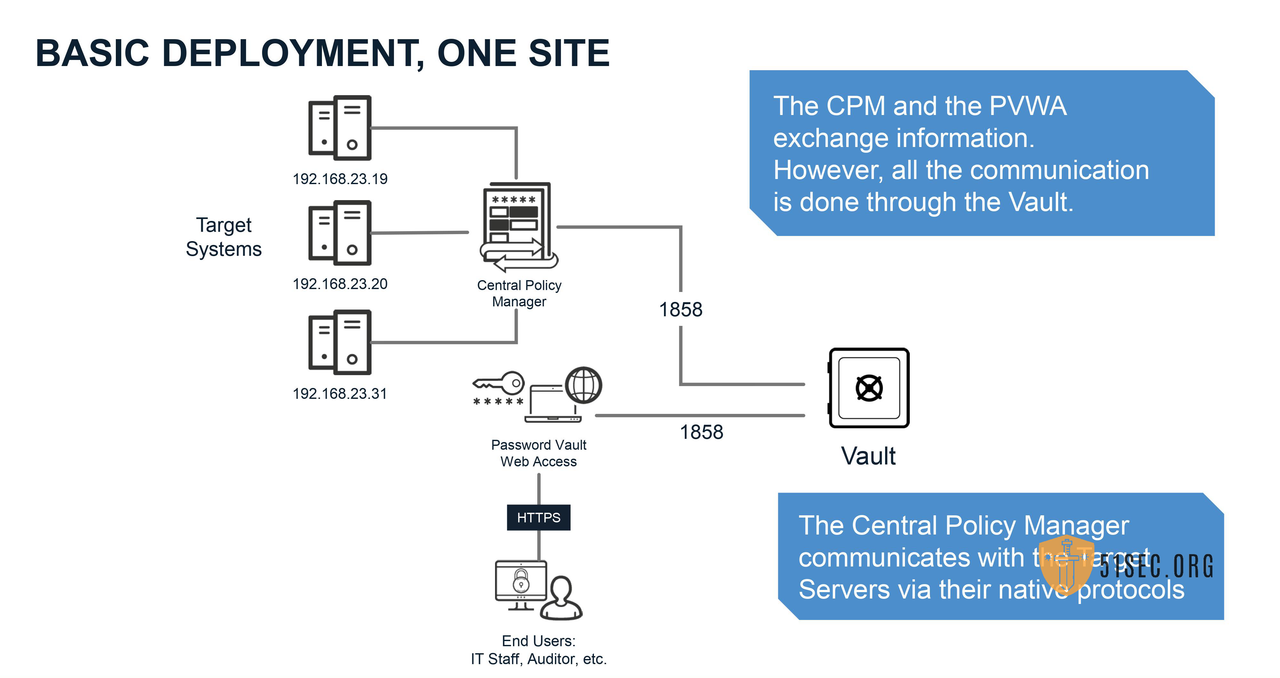
Native protocol: tcp 1858
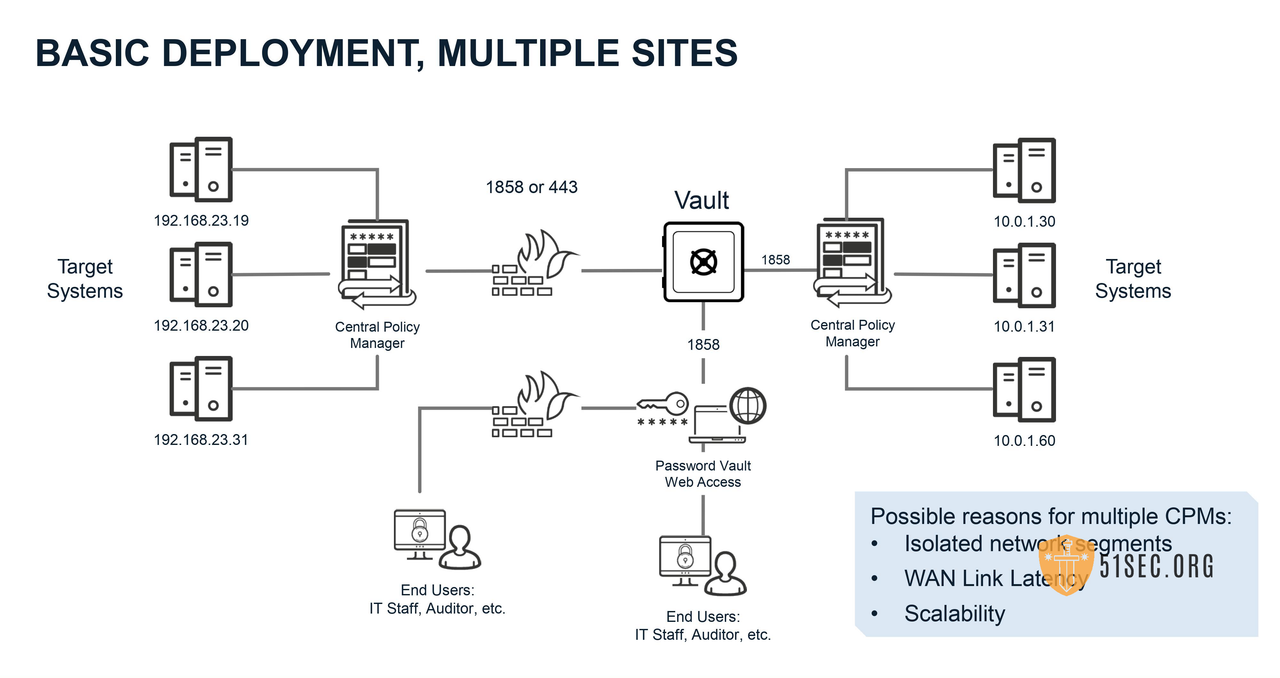
CyberArk Security Fundamentals







Summary
In this post we covered:
•The CyberArk Components that comprise the Core Privileged Access Security solution.
•The Architecture of the EPV and PSM solutions.
•The key recommendations for protecting the CyberArk environment.







No comments:
Post a Comment